Data security safeguards digital information from unauthorized access, theft, and misuse through access controls, encryption, and DLP. It differs from data privacy, which governs how data is collected and shared. Effective security demands strong authentication, monitoring, and compliance with frameworks like GDPR, HIPAA, and PCI DSS. Tools like Netwrix Endpoint Protector enhance protection by securing endpoints, preventing data leaks, and enforcing encryption policies.
What is data security?
Data security is frequently defined as a set of safeguards designed to prevent unauthorized access and theft of digital data. These measures cover everything from the security of various software layers to configurations and underlying policies and procedures.
Some of the most common technologies and mechanisms used for data security are:
- Access controls: All mechanisms that limit who can access data and what they can do with it. This includes user authentication as well as determining who has permission to read and write specific data.
- Encryption: Using complex algorithms and encryption keys to transform plain text data into a form that is unreadable without the correct decryption key.
- Data loss prevention (DLP): Systems that prevent users from sharing data outside the organization, either accidentally or intentionally. Today’s DLP systems go even further by automatically detecting sensitive data.
Although there are many other ways to protect your organization’s data, other information security measures like on-premises physical security controls (locks, guards, etc.), network and web security (firewalls, vulnerability scanners), or disaster recovery and business continuity (for instance, data backups) are typically not included in the definition of data security.
Why is data security important?

Data security is becoming increasingly important for all types of organizations as time passes. While it was considered a lower priority only about ten years ago, many businesses now consider data security to be a requirement for market survival. Here are some of the reasons why data security is so important today:
- Global digitalization: Data that was previously stored in various ways is now all stored digitally. While digital systems were initially focused on simple text and numbers, almost every document is now handled digitally, making data the focal point of business.
- Global accessibility: It seems like only yesterday that data was stored in server rooms in the back of company offices and accessed via local network computers. This is now a thing of the past, with data being primarily hosted in massive data centers in the cloud and accessible from anywhere via the Internet.
- Increased sensitivity: As new technologies and applications penetrate deeper into our lives, digital systems store more and more sensitive data. It’s not just our passwords or security codes; it could now be our entire gene sequences or detailed medical history.
- The age of digital crime: The expanded scope, depth, and value of data benefits not only us and the businesses we work with but also criminals. Criminal organizations no longer organize elaborate bank robberies. Instead, they find your digital vulnerabilities, perform cyberattacks, steal your information, and sell it on the black market to the highest bidder, who will use it against you. The data is no longer threatened by inquisitive and harmless teenage hackers from 1980s movies like War Games but by organizations worthy of Al Capone.
Because of the importance of data in today’s world, and thus the importance of data security, no organization can function without a comprehensive security approach that prioritizes data security.
Benefits of data security
With today’s plethora of cybersecurity approaches, some would argue that data security does not merit being treated as a separate discipline. Today’s integrated email security solutions, for example, may include measures that detect and block attempts to send sensitive data via the SMTP protocol. However, taking this approach to data security diminishes its significance and makes it very easy to overlook major gaps.
Instead, if your organization prioritizes data security and does not treat it as a subset of other IT security disciplines, you will reap several benefits:
- A focused approach to data security ensures that there are no gaps, regardless of the other approaches, systems, and mechanisms used. This is because you are concentrating on the data itself rather than the methods for accessing it.
- Most organizations nowadays must meet strict regulatory compliance requirements in order to conduct business in a specific field and geographical area, and this includes almost every company that stores any type of critical data, not just fintech or medical. Because compliance, like data security, makes data the focal point, a well-rounded approach to data security allows businesses to easily meet such requirements and avoid costly fines.
- You make your customers feel safer by focusing on data security and discussing it with them. This, in turn, not only improves retention but also increases the likelihood that your products and/or services will be recommended to others. It also makes for excellent marketing when discussed publicly. A thorough approach to data security is, in essence, your best digital business card, demonstrating that you take your company and its customers/partners seriously.
Caring for your data security begins, of course, with defining your needs and developing a comprehensive strategy, followed by tactics and determining the best solutions for your needs. Even when using integrated data security solutions, these must be viewed holistically and not taken for granted.
Data security vs. data privacy
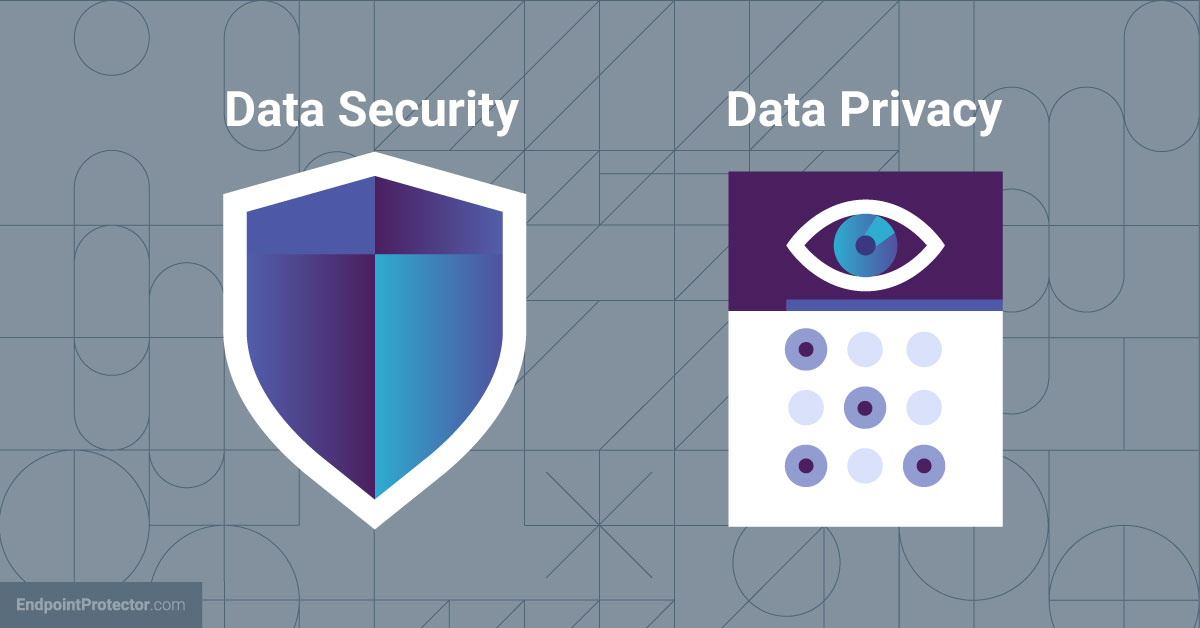
The terms data security and data privacy are closely related, but they are frequently confused and misunderstood. While, as previously stated, data security is concerned with safeguarding sensitive data against unauthorized access and theft, data privacy is concerned with safeguarding the interests and rights of individuals whose data is being collected and processed. Although the two concepts are related and frequently overlap, the implementations of data security and data privacy are completely different.
For example, consider a healthcare professional who gathers and keeps patients’ personal data along with their health information and detailed medical records. Protection of the records’ availability, confidentiality, and integrity would be the main goals of data security methods. For instance, the service provider might employ access controls to guarantee that only authorized personnel can read the records or use encryption to secure the data from unauthorized access.
On the other side, data privacy regulations would concentrate on regulating how that data is gathered, used, and shared. To guarantee that the data is only accessed and released in compliance with applicable laws and regulations, the provider may, for instance, get the patient’s consent before collecting and retaining their data, give notice of how the data will be used, and adopt policies and procedures.
Best practices for ensuring data security
It’s worth looking at industry best practices when starting your data security journey as well as when reevaluating your current position. By ensuring that you have covered all of the following bases, you can be confident that your data security strategy is both comprehensive and effective.
- Create and implement a comprehensive data security plan: Organizations should have a plan that outlines data security policies, procedures, and protocols. Access control, data encryption, employee training, incident response, and disaster recovery should all be covered in this plan.
- Don’t underestimate the power of training: Employees should be trained on data security best practices, such as recognizing and responding to security threats, as well as using company systems and resources securely. This both improves their skills and reduces the likelihood of data security incidents occurring, as well as raises their awareness of the critical importance of data security.
- Use encryption for sensitive data: With today’s computers’ efficiency, there is no reason not to use encryption. When possible, all sensitive information should be encrypted. Data encryption should be used for data in transit as well as data at rest.
- Limit data access: User access should be restricted as much as possible to only those employees who need it to perform their job functions. Role-based access controls, for example, can help ensure that only authorized users have access to sensitive data.
- Monitor your data security: No matter how many systems you have in place or how effectively the automation is set up, you need to keep an eye on your data security and be on the lookout for any unusual activity. In the sphere of data security, it is preferable to occasionally deal with a false positive rather than run the risk of data breach consequences.
- Perform regular security audits and assessments: Regular security audits and assessments can assist in locating potential weaknesses and opportunities to improve security practices.
- Make use of the appropriate software: In the field of data security, the right software can make all the difference. Based on your needs, as defined in your data security plan, you should choose one or more security solutions that not only meet your current data security requirements but also allow you to scale easily as your business grows.
- There will never be effective data security without associated data management/data governance and data resiliency measures: To provide effective data security, your data strategy must be as comprehensive as your cybersecurity strategy, which includes data security as one of many topics.
Types of data security measures
There are many security measures that can be implemented as part of your data security program. Here are some of the most often-used ones:
- Sensitive data identification and classification: Identifying and classifying data that can be considered sensitive information is one of the most difficult challenges in data security. If this process is done manually, it requires a significant amount of resources and time to complete if there is any initial data storage to process, making it not only uneconomical but frequently impossible. Fortunately, with today’s advances in artificial intelligence, much of the identification and classification can be done automatically.
- Authentication, authorization, and access management: Another layer of complexity in data security comes from determining who should have access to specific types of data, what type of access should be granted, and how to ensure that the person is who they say they are. With the complexity of today’s social engineering attacks, simple passwords are frequently insufficient, so user authentication and authorization frequently include biometric systems, multi-factor authentication, and more.
- Data encryption: When compared to even 20 years ago, today’s computers and even mobile devices are so powerful that no one is concerned about the overhead of data encryption. Most Internet protocols, such as HTTPS for web pages and SMTPS for email servers, are now based on TLS (Transport Layer Security), which is a combination of symmetric and asymmetric encryption. A data security program, on the other hand, must go much further, employing both symmetric (the same key is used to encrypt and decrypt) and asymmetric (different keys are used to encrypt and decrypt) encryption to the data itself, such as database content, files, USB memory sticks (pen drives), and more as well as handling related key management. The general consensus is that the more data you encrypt, the better your data security.
- Secure data sharing and data loss prevention: You may believe that once you have confidently identified sensitive data, securely authenticated the user, granted that use only the necessary access rights, and encrypted as much data as possible, your job is done. Unfortunately, due to human error and malicious intent, this is not the case. An authenticated user may manually decrypt the data and share it with someone outside of your organization. They may do so unintentionally, as a result of a social engineering attack, or to cause harm to the organization. This is why data loss prevention solutions should be the focus of your data security program, especially since such solutions frequently include identification, classification, and encryption functionality.
- Data masking, automatic data erasure, and more: The mechanisms listed above are not the only ones that could be included in your data security strategy. More technologies and techniques can be used; for example, sensitive data can be masked by replacing it with elements such as secure hashes or through tokenization, sensitive information can be automatically removed from endpoint devices after a certain time, and so on. Leading-edge DLP solutions frequently include more exotic functions, and investing in dynamically developing solutions is your best bet for having any new approaches ready to try in the future.
Only the most fundamental security measures are included in standard operating systems or other cybersecurity software. To implement the majority of the measures listed above, you must first select a data security implementation strategy:
- A stand-alone approach focuses on implementing systems and mechanisms dedicated solely to data security and includes very few other cybersecurity-related functionalities. This primarily refers to dedicated enterprise DLP systems. This approach ensures that all data security needs are met, but you must also make sure that all your technologies are covered. For example, managing mobile app data security may necessitate the use of solutions that differ greatly from those used to manage laptop/desktop data security.
- An integrated approach focuses on specific channels used to handle and transfer data. An integrated email security solution, for example, may include measures to detect and eliminate phishing and other social engineering attacks, prevent viruses, ransomware attacks, and other malware, as well as detect and prevent the sharing of sensitive data in emails, and provide the option to encrypt email content. However, for obvious reasons, such a solution is ineffective in preventing data sharing via social media, so your data security plan must include other integrated (or stand-alone) solutions to handle other channels.
Data security risks
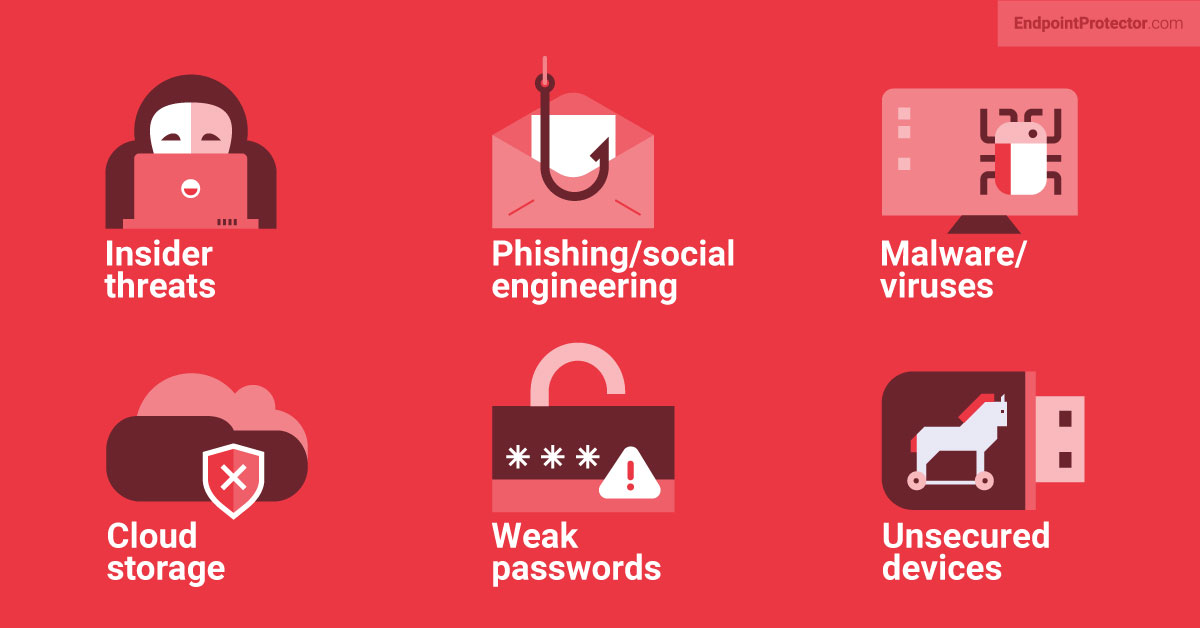
Defining potential data security risks is one of the most important steps in defining your data security strategy, which should serve as the foundation for everything else you do in relation to data security. While the list of all potential data security risks is lengthy and complex, not every business will face all of them, depending on the type of sensitive data handled and how it is handled. Here are some of the most important data security risks to consider during risk analysis:
- Insider threats: Insider threats occur when someone who is authenticated and authorized to access data shares it with an unauthorized third party, either accidentally or on purpose. Contrary to popular belief, this is more often than not unintentional. Because of the number of cases and the complexity of defense against them, insider threats are frequently regarded as the most serious threat to data security.
- Phishing/social engineering: Social engineering attacks, such as phishing, frequently result in unintentional insider threats. Attackers are becoming increasingly sophisticated, and many people have difficulty distinguishing between a phishing attack and a genuine message, especially since much phishing is now carried out via mobile phones, which lack social engineering protection. Data security is not about preventing attacks (that is the job of other types of software) but about preventing the consequences – not allowing the user to share the data they have been duped into exposing.
- Malware/viruses: A lot of malware and viruses, like social engineering attacks, require user interaction, and the more sophisticated ones can elude even the most professional antivirus/anti-malware software. Unlike social engineering, viruses/malware typically aim to either destroy or make inaccessible the data on the endpoint device, enable third-party access to the device, or escalate to other attached devices via the network or credentials stolen from the attacked device. The best defense against this, in conjunction with specialized software, is to not have unencrypted sensitive data on the device, i.e. enforced encryption or deletion of any sensitive data downloaded locally after a short period of time.
- Cloud storage: With the majority of business applications now transitioning or having already transitioned to Software-as-a-Service (SaaS) models, sensitive data is no longer stored on equipment owned by the organization but rather handled by third-party organizations. While such deals are, of course, legally protected, a security breach can have consequences that a good contract cannot protect against, such as loss of reputation and customers. That is why, in the age of the cloud, the best way to improve your data security is to store all data strongly encrypted – this way, even if it leaks, the attackers cannot use it in any way.
- Weak passwords: Passwords are the most widely used authentication mechanism, but they are also the least secure. Businesses exacerbate the problem by attempting to force password complexity rather than length (while the length is far superior for security) and by requiring users to change passwords on a regular basis (which causes users to reuse the same passwords with minimum modification, greatly reducing password security). So, in general, organizations are shooting themselves in the foot, and the best approach to data security would be to invest in multi-factor authentication using hardware keys and/or biometrics. If you can’t do that, just stop forcing password changes and allow users to use all lowercase as long as the password is longer than 16 characters.
- Unsecured devices: One of the most significant challenges that organizations are now facing is the widespread use of mobile devices for work purposes. While laptop and desktop data security software is already mature and capable of providing everything required, mobile phones have advanced too quickly, and we’re still at a point where it’s much easier to prohibit access to sensitive data via mobile phones rather than trying to secure them effectively. Organizations must exercise extreme caution in terms of data security when granting access to sensitive data via mobile apps and devices until reliable software is available to provide comprehensive data security on mobile devices.
Data security regulations
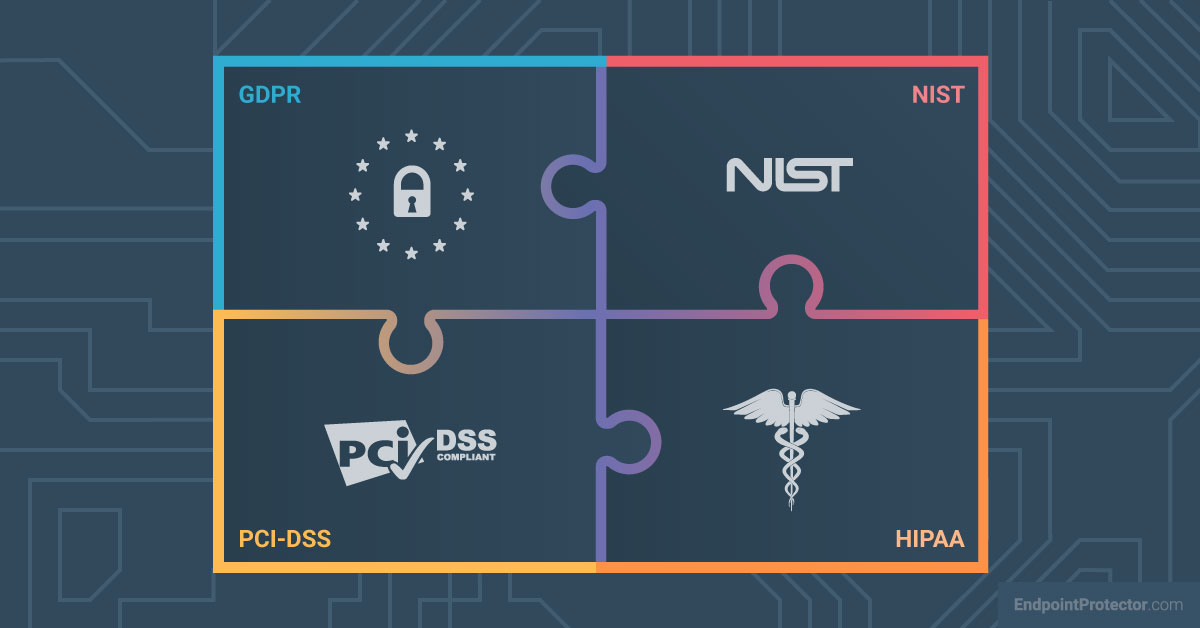
As previously stated, many organizations today must meet stringent regulatory compliance requirements in order to conduct business. Some of the most important regulations for specific fields and geographical areas are listed below. These regulations elevate data security above the level of nice-to-have best practices. While these regulations frequently do not define specific data security measures as hard-wired requirements, maintaining compliance is impossible unless some scope of data security is included in your IT security strategies.
- GDPR: The General Data Protection Regulation was established by the European Union in 2018. The GDPR requires organizations that process EU citizens’ personal data (also known as personally identifiable information – PII in the US) to implement appropriate technical and organizational safeguards to ensure data security.
- HIPAA: The Health Insurance Portability and Accountability Act is a federal law in the United States that has been in effect since 1996 and establishes national standards for the protection of medical records and other personal health information. HIPAA requires entities such as healthcare providers and insurers to have administrative, physical, and technical safeguards for electronically protected health information (ePHI).
- PCI DSS: The Payment Card Industry Data Security Standard is a set of security standards created in 2004 by major credit card companies to combat payment card fraud. PCI DSS requirements cover a wide range of data security measures, including cardholder data encryption, access controls, and vulnerability management, as well as security system monitoring and testing. The standards apply to any organization that accepts payment cards, including merchants, processors, and financial institutions.
- CCPA: The California Consumer Privacy Act has been in effect since 2020 and applies to businesses that collect and process personal information from California residents. The law requires covered businesses to provide consumers with certain notices about their data collection and use practices, as well as to implement reasonable data security measures.
- NIST Cybersecurity Framework: The National Institute of Standards and Technology’s Cybersecurity Framework is a set of guidelines and best practices to manage and reduce cybersecurity risk through the entire lifecycle of the organization. The framework is voluntary but widely used in both the public and private sectors. Its specific data security requirements include implementing access controls, using encryption to protect sensitive data, and regularly monitoring and auditing data access.
How does Endpoint Protector help with data security?
Endpoint Protector may appear to be just another knight on your data security chessboard, but it could be the key to avoiding a checkmate. It is very likely that your data security strategy will identify data classification, encryption, and insider threat protection as some of the most critical issues to address and that the majority of your workforce accesses data via laptop or desktop endpoints. If that’s the case, there’s no better place to start than by moving that Endpoint Protector knight from g1 to f3.
Here are some of the key issues that Endpoint Protector can help you address:
- The Device Control feature allows you to lock down, control, and monitor USB and other peripheral ports. This helps you avoid insider threats caused by your employees moving sensitive data from their protected devices to unprotected data storage, either accidentally or on purpose.
- The Content-Aware Protection feature prevents sensitive data from being transferred to insecure removable devices, emails, chat messages, and more. It is very effective in preventing insider threats because it eliminates the channels through which data can leave a secure environment.
- The eDiscovery feature makes sensitive data identification and classification a breeze. You can configure automatic scans or manually inspect the device’s content, as well as delete sensitive data that should not be stored on the device in an insecure manner, such as in unencrypted text files.
- Last but not least, you can encrypt, manage, and secure USB storage devices with the Enforced Encryption feature. This allows you to use insecure storage devices while still ensuring data security.
Frequently Asked Questions
The 5 key ways to secure your data are:
1. Create and implement a comprehensive data security plan;
2. Train your employees and make them aware of the importance of data security;
3. Limit data access as much as you can;
4. Use encryption for all sensitive data;
5. use appropriate software, such as Endpoint Protector, that covers most of your bases in one go.
Download our free ebook on
Data Loss Prevention Best Practices
Helping IT Managers, IT Administrators and data security staff understand the concept and purpose of DLP and how to easily implement it.












