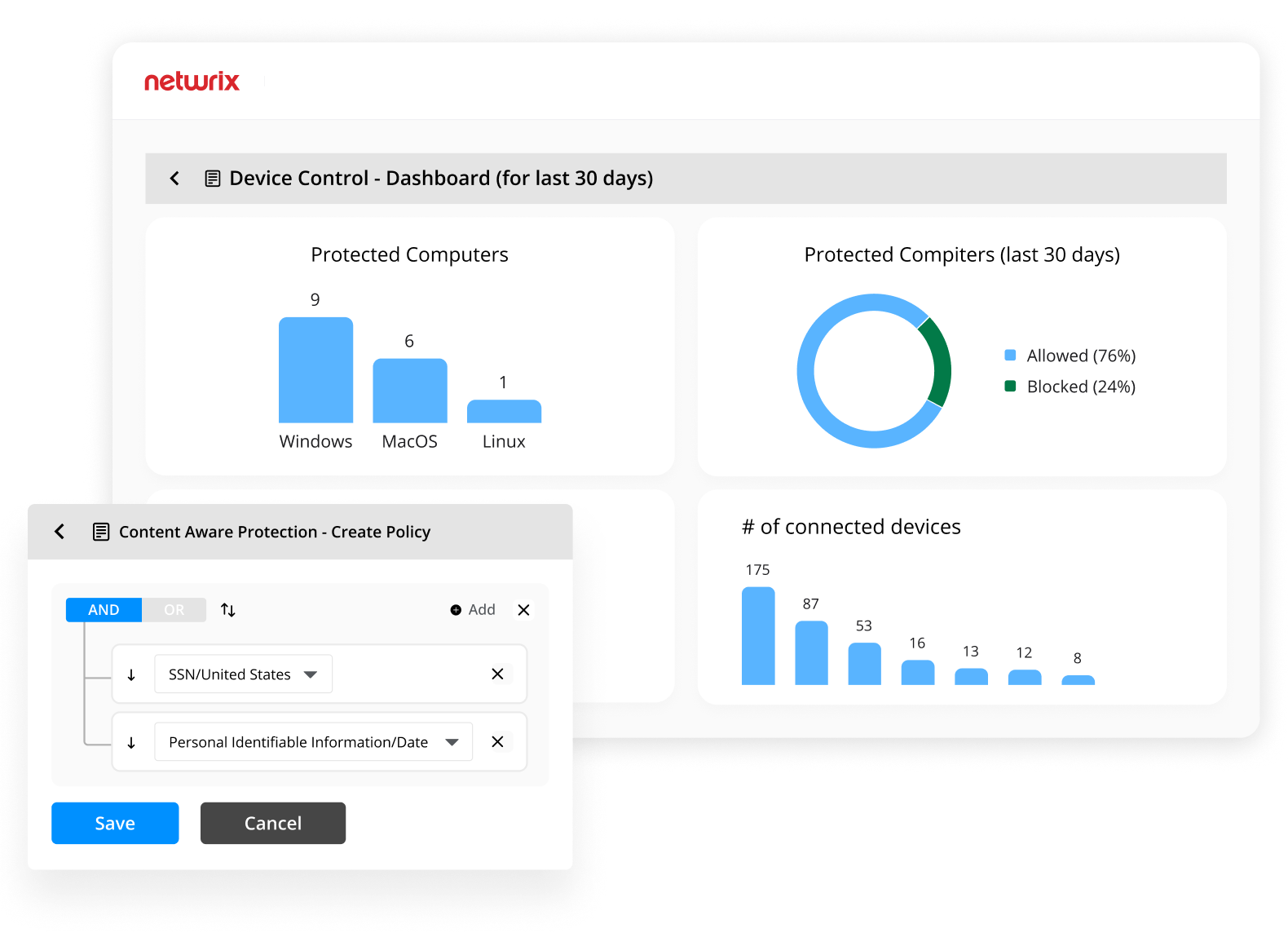
Are Your Endpoints Following Policy - or Hoping for the Best?
Unmanaged devices and loose policies are an open invitation for insider threats. USB drives, file transfers, and misconfigurations remain leading causes of data loss and ransomware entry. With Netwrix, you gain continuous protection - before data ever leaves the device.

Real-Time file transfer control
Block or allow file movement based on content, user, or destination. Enforce smart rules across email, cloud apps, browsers, and chat platforms.

Multi-OS Endpoint Security
Protect Windows, macOS, and Linux endpoints with lightweight agents and centralized control—whether devices are on-site or remote.

USB & Peripheral Device Security
Enforce encryption, block rogue USBs, and prevent unauthorized access to removable media. Build trust without sacrificing usability.