
The foundation for today’s increasingly digitized world must be built upon trust and transparency. If people don’t feel in control of their personal data and how it’s used, they’ll fail to trust the data-driven digital services that carry so much potential for economic growth and innovation. The General Data Protection Regulation (GDPR) is the European Union’s (EU) attempt to build citizens’ trust in the digital age by harmonizing standards for data protection across the EU.
With the official regulation document running to 88 pages, 99 articles that dictate the compliance requirements, and over 50,000 words, GDPR is a complex data protection law that continues to cause challenges and confusion for businesses of all sizes. This comprehensive GDPR compliance guide distills the regulation into the most crucial points while focusing on simple and practical language to assist with your compliance efforts and help avoid substantial fines for breaches of GDPR rules.
What is GDPR, and how might it impact your business?
GDPR is a unified data protection law that provides stronger data privacy rights for individuals and sets out important rules for organizations to follow when processing personal data belonging to any citizen or resident of an EU member state. These rules act as safeguards to prevent the misuse of personal data.
GDPR is regarded as the strictest of the world’s data privacy laws, and it set the benchmark for other similar regulations that followed in its footsteps, such as the California Consumer Privacy Act (CCPA).
GDPR functions as a regulation rather than a directive. Under EU law, regulations are laws that apply to any EU member state and that dictate orders and rules to abide by. A directive, on the other hand, sets out a result to achieve without dictating how to achieve that result.
Before getting to the business impacts of GDPR and unpacking the key points from Europe’s flagship data protection act, there is some important terminology to clarify:
- Data controllers are natural or legal persons, public authorities, agencies, or other bodies that, alone or jointly with others, decide how and why to process personal data.
- Data processors are entities that process data upon the instruction of a data controller. Examples of entities that might strictly act as data controllers are email service providers or cloud-based storage service providers.
- Data subjects are living individuals whose personal data is collected, held, or processed by an organization.
GDPR has a wide range of potential impacts on businesses, including changing customer data security processes, facilitating data subject rights, and facing the consequences of failing to comply. Here are some specific things to think about.
- Mapping your data flows – Full visibility into data flows in and out of your organization is imperative for GDPR compliance. Whether for preventing a data breach, keeping records of processing activities, or fulfilling data subject access requests, understanding where data is and how it’s being used requires a data inventory, which may require a large-scale effort depending on your current level of visibility.
- Improved cybersecurity measures – GDPR calls for risk-based measures to ensure the confidentiality and integrity of customer data. This may entail putting in place technical or structural solutions that you don’t currently use, such as encryption, pseudonymization, and compliance testing.
- Non-compliance consequences – Aside from the large fines and sanctions for non-compliance, other consequences that could impact your business include data subjects bringing civil claims against you, brand damage, and loss of trust.
- Marketing impacts – GDPR rules for data protection can have significant impacts on marketing activities, including both the time and cost of marketing. More precisely, the data protection principles require you to always choose and justify appropriate lawful grounds for processing data and use proper opt-ins. You also need to take more care regarding the information you store, share, and use from social media websites or social networking platforms like LinkedIn.
- Employee training – Since most data breaches and other mishaps come from human error, GDPR compliance requires an organization-wide approach with suitable training on data protection matters. Training is particularly important for any staff directly involved with personal data processing, whether that means a receptionist, an IT engineer, a product developer, or someone on the board of directors.
The history and evolution of GDPR
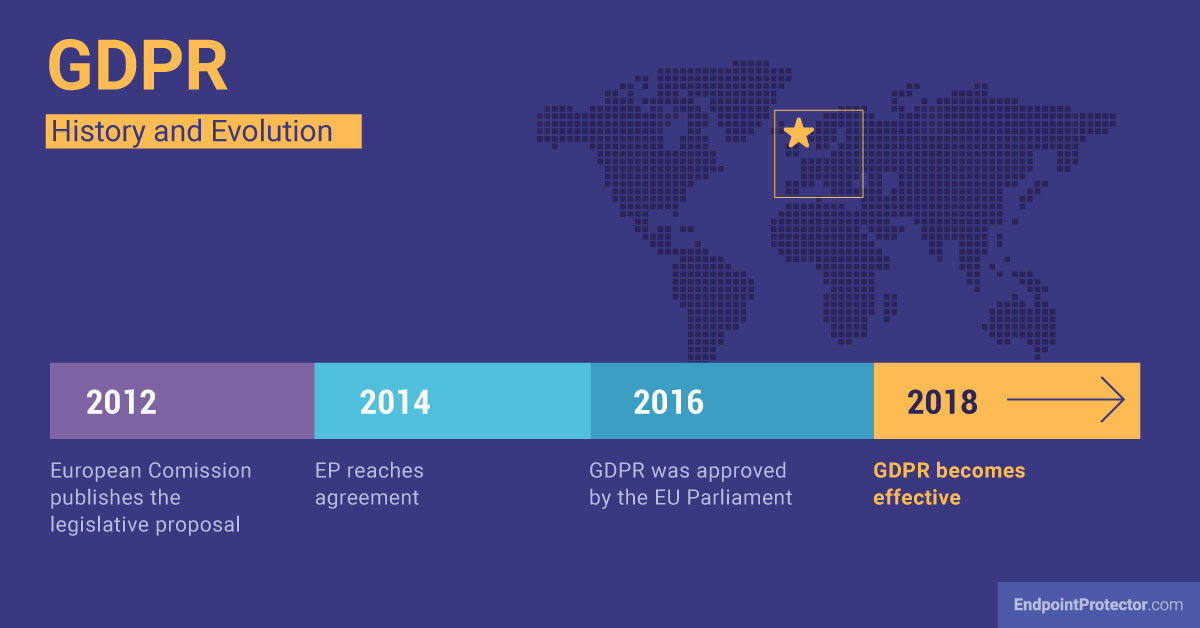
GDPR replaces the Data Protection Directive of 1995, which was set out jointly by the European Parliament and the European Council, and became effective on May 25, 2018.
Issued by the European Commission, the European Parliament, and the Council of Ministers of the EU, GDPR is the most important change in data privacy regulation in 20 years. It took four years of preparation and debate until it was finally approved by the EU Parliament on April 14, 2016.
The GDPR makes a big statement about individuals’ private data and their right to request data controllers and processors to delete, correct, and forward their data. In consequence, GDPR brings significant changes to its predecessor, the Data Protection Directive, which requires operational changes in organizations and imposes major fines in case of failure to protect EU data subjects.
Key articles under the GDPR
Cross Border Cases
According to Article 3, the GDPR applies to the processing of personal data in the context of the activities of an establishment of a data controller or a data processor in the EU, regardless of whether the processing takes place in the EU or not. This means that any company that makes its website or services available to EU citizens, including US companies, must be GDPR compliant.
Data Breach Reporting Obligations
GDPR contains clear and comprehensive reporting obligations both to supervisory authorities and data subjects in the event of a breach. When a data breach involves some risk to the rights and freedoms of data subjects, you must report to the relevant supervisory authority without undue delay or no later than 72 hours after becoming aware of the breach. Where a data breach involves high levels of risk to data subjects’ rights and freedoms, a breach notification must be sent to the affected individuals without undue delay.
Lawful Purpose and Informed Consent
GDPR is very strict about the grounds for processing data. Unlike in many other countries or jurisdictions, it’s not lawful to collect data first and justify it later; you need a lawful reason to process personal data. Furthermore, you need to be transparent about this purpose and ensure that people can show their consent either with a statement or as a clear affirmative action.
Record-Keeping
One of the key articles in GDPR is that it’s not enough to just comply with the rules, your organization also needs to document the fact that you are in compliance. A big part of this is Article 30, which mandates keeping written or electronic records of processing activities if you have 250 employees or more. If you have fewer than 250 employees, the record-keeping obligation still applies if the processing is likely to result in a risk to the rights and freedoms of data subjects, is not a once-off, or includes special category data or criminal conviction data.
Appointing A Data Protection Officer
GDPR introduces an obligation to appoint a Data Protection Officer (DPO) for organizations that fit into one of four categories:
- If you’re a public authority,
- If your core activities consist of regular and systematic monitoring of data subjects on a large scale,
- If your core activities consist of processing special categories of personal data on a large scale, or
- If EU member state law requires the appointment of a DPO.
Who does GDPR apply to?
GDPR applies to all businesses and organizations that process personal data about EU citizens and residents. The rules apply regardless of where the processing of personal data takes place for companies based in or with branch offices in the EU.
It’s pivotal to grasp the fact that GDPR has significant extraterritorial scope. What this means is that being established as a business or non-profit outside of the EU doesn’t necessarily mean you don’t need to comply. If either of the following facts holds true about your organization, you need to comply with GDPR’s data protection rules:
- You offer goods or services (including services where no payment is required) in which you process data belonging to EU data subjects (citizens and residents).
- You monitor the behavior of EU data subjects, such as by monitoring website traffic and tracking users with cookies.
This wide territorial scope captures the full proliferation of data-driven digital technologies and the various ways in which member state data subjects can have information collected about them even from organizations established outside the EU.
A persistent myth about GDPR is that it doesn’t apply to organizations with fewer than 250 employees. There is no size threshold for GDPR compliance. This myth perhaps stems from the fact that there is a potential exemption from GDPR’s record-keeping obligations for organizations with fewer than 250 employees. However, compliance with the remainder of the regulation is still mandatory regardless of the size of your organization.
The 7 principles of the GDPR
Seven guiding principles lie at the heart of how GDPR aims to ensure data privacy and otherwise protect personal data across the EU and European Economic Area (EEA).
1. Accountability
The accountability principle runs through the entirety of GDPR compliance, and it puts the obligation on organizations to not only put the correct technical and structural measures in place for compliance but also to be able to demonstrate how they comply with GDPR requirements.
2. Lawfulness, fairness, and transparency
This principle states that processing activities must be conducted lawfully, fairly, and in a way that’s transparent to the data subject.
- Lawfulness means that you process personal data only based on one of the six lawful grounds set out under GDPR. For special categories of data (e.g., biometric data), the processing is only lawful under a more restricted set of conditions.
- Fairness means not deceiving or misleading data subjects with your data collection activities. This requires accounting for the way in which data subjects could be impacted by your use of their data, such as in cases of profiling. Fairness also applies to how you deal with data subject access requests and other data subject rights.
- Transparency requires your organization to be open and clear to data subjects about the processing of personal data. Important elements here include avoiding jargon and having information about data processing activities easily accessible.
3. Purpose limitation
Purpose limitation means you can only collect data for a legitimate and specific purpose that you’ve informed the data subject about. Typically, if you want to use the data for any other purpose, you need to obtain fresh consent.
4. Data minimization
The data minimization principle requires you to identify and collect only the minimum quantity of personal data required for the specific purpose you’ve previously outlined and informed the data subject about. This principle helps avoid situations where organizations collect more data than what’s necessary or relevant for their purpose in case they might need this data in the future.
5. Accuracy
The accuracy principle mandates that you take reasonable measures to ensure personal data is both up-to-date and factual. This includes cases where a data subject exercises the right to rectification of inaccurate or out-of-date personal data so that you correct or update the information.
6. Storage limitation
The storage limitation principle is another rule that traces back to the purpose of processing personal data. This principle mandates that you don’t keep personal data for any longer than it’s needed based on the legitimate purpose for which you process it. You can retain data for longer periods when it’s processed solely for public interest archiving, scientific or historical research, or statistical purposes.
7. Integrity and confidentiality
This is the main data security principle of GDPR and states that you must have appropriate security measures in place to protect the personal data you hold. Cybersecurity enters the equation in terms of how you protect electronic information and the systems on which you store data. An important point about this principle is that it doesn’t define a specific set of security controls to implement; rather, it states that you should implement security measures that are proportionate to the risk that your processing poses.
Data subject privacy rights
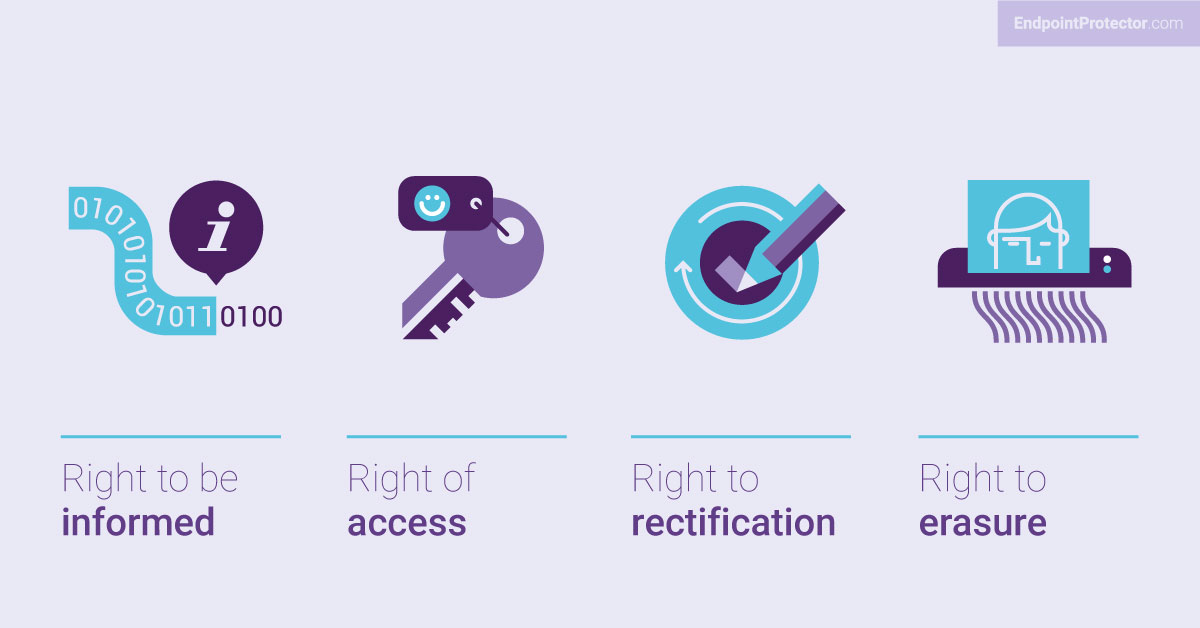
A key part of GDPR is the eight data subject privacy rights that the regulation outlines. Data controllers must be aware of these rights and facilitate any situations in which a data subject opts to exercise their rights. Data processors must also understand data subject rights so that they can pass on any requests to the data controller when an individual exercises their rights.
- Right to be informed – Honoring the right to be informed requires providing data subjects with concise and easily accessible information on what personal data is being collected about them and how it’s being used.
- Right of access – This gives data subjects the right to access their personal data and to make a request for this access either verbally or in writing.
- Right to rectification – Provides data subjects with the right to have inaccurate or incomplete information about them corrected or completed.
- Right to erasure – This gives data subjects the right to be forgotten; in other words, to request that you delete their personal data.
- Right to restrict processing – In certain circumstances, data subjects can request that their data be merely stored but any other processing is restricted. These circumstances include when someone contests the accuracy of their data or objects to its processing.
- Right to data portability – Data subjects have the right to obtain and reuse data for their own purposes by moving, copying, or transferring data given to a data controller.
- Right to object – Data subjects have the right to object to the processing of their data, and it’s important to inform individuals about this right from the outset the first time you communicate with them.
- Rights in relation to automated decision-making and profiling – Data subjects have the right not to be subject to a decision based solely on automated processing or profiling. Furthermore, since automated decision-making counts as high-risk processing, you need to conduct a Data Protection Impact Assessment (DPIA) to show you’ve understood and mitigated the risks of this kind of processing.
Penalties for GDPR non-compliance

Ensuring compliance is a pressing concern for companies of all sizes – whether they are processors or controllers – partly due to the severity of GDPR fines for breaches of the rules. The following two-tier system of fines applies for infringements of the rules:
- For severe breaches of the rules, maximum fines of €20 million or 4 percent of global turnover for the past financial year, whichever is higher
- For less severe breaches, maximum fines of €10 million or 2 percent of global turnover for the past financial year, whichever is higher. A country’s supervisory authority decides on the severity of the penalty using factors such as whether the infringement was intentional or negligent and the categories of personal data affected by the infringement.
Requirements for compliance
To be able to apply the enhanced, stricter rules that GDPR sets out, organizations should perform an audit of their current data security solutions and processes implementation and build upon it. The audit should reveal what data is collected from individuals, if there are proper consent procedures, where private details are stored, who has access to them, how the integrity of private data is ensured, etc.
Based on the discovered information, a solid plan for upgrading to the new regulation can be outlined and shared with all involved parties. Here are two key requirements to ensure compliance without expending too many organizational resources:
1. Disciplined execution
The strategy is worth nothing without disciplined execution. Knowing what data security and management solutions have to be selected and implemented to ensure compliance and security is not as easy as it might seem. There are numerous factors that weigh in and the human factor is the most complex.
A simple example would be that a DPO has to be appointed. Companies have a tough decision to make, considering the level of responsibility assigned to a DPO. The officer has to make sure that data protection compliance is met. Their role is crucial and difficult, having to deal with employees on one side and department managers on the other.
Also difficult to execute is the article referring to the cross-border transfers which extend farther than the physical borders where the headquarter or branches of a company are located. A company operating in Germany can have customers in France, the US, or any other country. This comes with a big responsibility concerning individuals’ data security.
The GDPR applies to the processing of personal data of individuals residing in the EU, even if the data controller or processor is not located in the EU. So, if your business is not in the EU, you can still be subject to the regulation.
2. Awareness
Chief Security Officers, IT managers, CEOs, business unit managers, etc. have to be informed of the legal changes the GDPR implies and should make sure they translate them into plain, simple measures to apply in order to respect the regulation.
The clearer the objectives are, the sooner everyone will understand what their role is and act accordingly. All department managers, top managers, and other decision-makers should carefully read the GDPR, or get advice from a lawyer regarding the obligations stated in the regulation.
The terminology used in this type of regulation is often difficult to understand, so asking for a lawyer’s advice is recommended, if not mandatory. Having full awareness of a company’s obligations concerning private data protection represents a solid foundation for the next steps.
Your assignment is to identify what data you store and process for EU data subjects, its location, its path from point A to B, by what systems it is processed, etc. By doing that, you can further realize if you have the required tools to protect sensitive company data, or what tools you may need to help you achieve GDPR compliance.
A real game-changer will be the ‘data protection by design and by default’ principle. This requires services or products to include privacy and security features from the very beginning of concept and development.
This awareness of security and privacy features from the outset will be of special interest to mobile app developers and the IoT sector. The new regulation will be a great motivator for vendors to align data security with innovation and build not only ingenious products but also secure products.
Beyond the product or service reference, the privacy by design principle should be applied also to other organizational processes, according to the GDPR rules. Basically, for any organizational process, whether it is operational, logistic, internal communication, HR, or any other process involving private data, companies must take into consideration security as a pillar with the same importance as any other element.
Why Endpoint Protector?
Endpoint Protector is an industry-leading Data Loss Prevention (DLP) solution that fully supports GDPR compliance and helps your organization avoid the costly consequences of breaches. Endpoint Protector works across multiple operating systems at the endpoint that often present the biggest compliance headaches and sources of risky behavior with personal data.
More specifically, the following features help with GDPR compliance:
Device Control
With Device Control, you can lockdown, control, and monitor USB and peripheral ports to stop data exfiltration. You can create device whitelists and blacklists, and define policies per user for granular control that reduces the risk of accidental or intentional GDPR compliance violations. You can also enforce encryption remotely for USB drives and other removable media.
Content Aware Protection
A content aware solution protects sensitive data by using policy-based rules to detect and block the transfer of GDPR-protected data outside your network. This level of awareness and transparency, which accounts for both content and context, minimizes the risk of data leaks and data losses and helps align with GDPR’s data protection by design and default article. Another benefit of Content Aware Protection is that the monitoring and control capabilities help ensure data is only used for the purpose for which you collect it, as required by GDPR’s purpose limitation principle.
eDiscovery
The foundation for GDPR compliance starts with mapping data flows so that you know where sensitive data is and how it’s being used. Conducting this task manually is difficult, prone to inaccuracies, and time-consuming given that sensitive data could reside on any endpoint device. Endpoint Protector’s eDiscovery automatically and efficiently scans and identifies personal data at rest on all the endpoints in your organization across Windows, macOS, and Linux computers.
Download our free ebook on
GDPR compliance
A comprehensive guide for all businesses on how to ensure GDPR compliance and how Endpoint Protector DLP can help in the process.
















