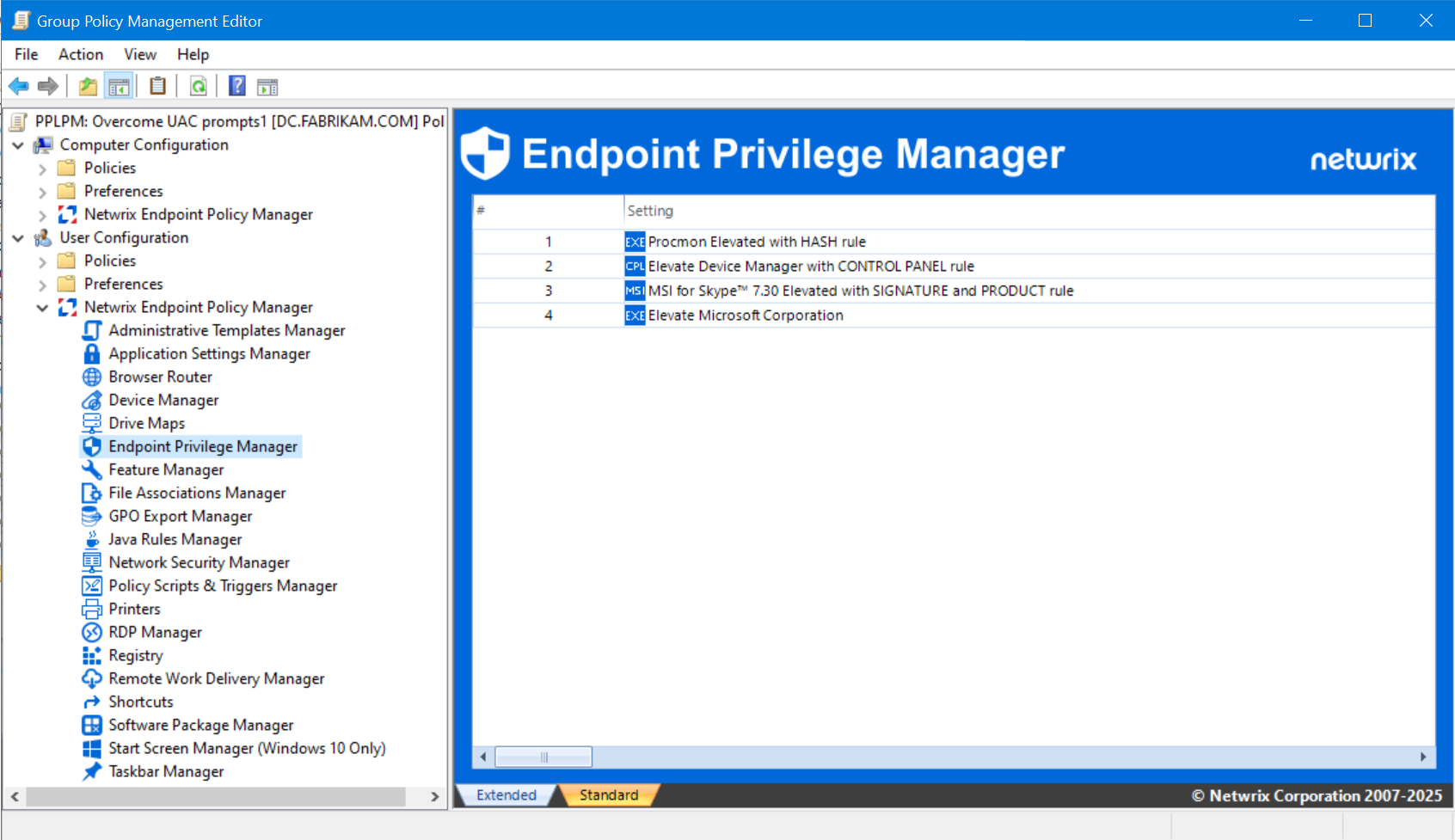
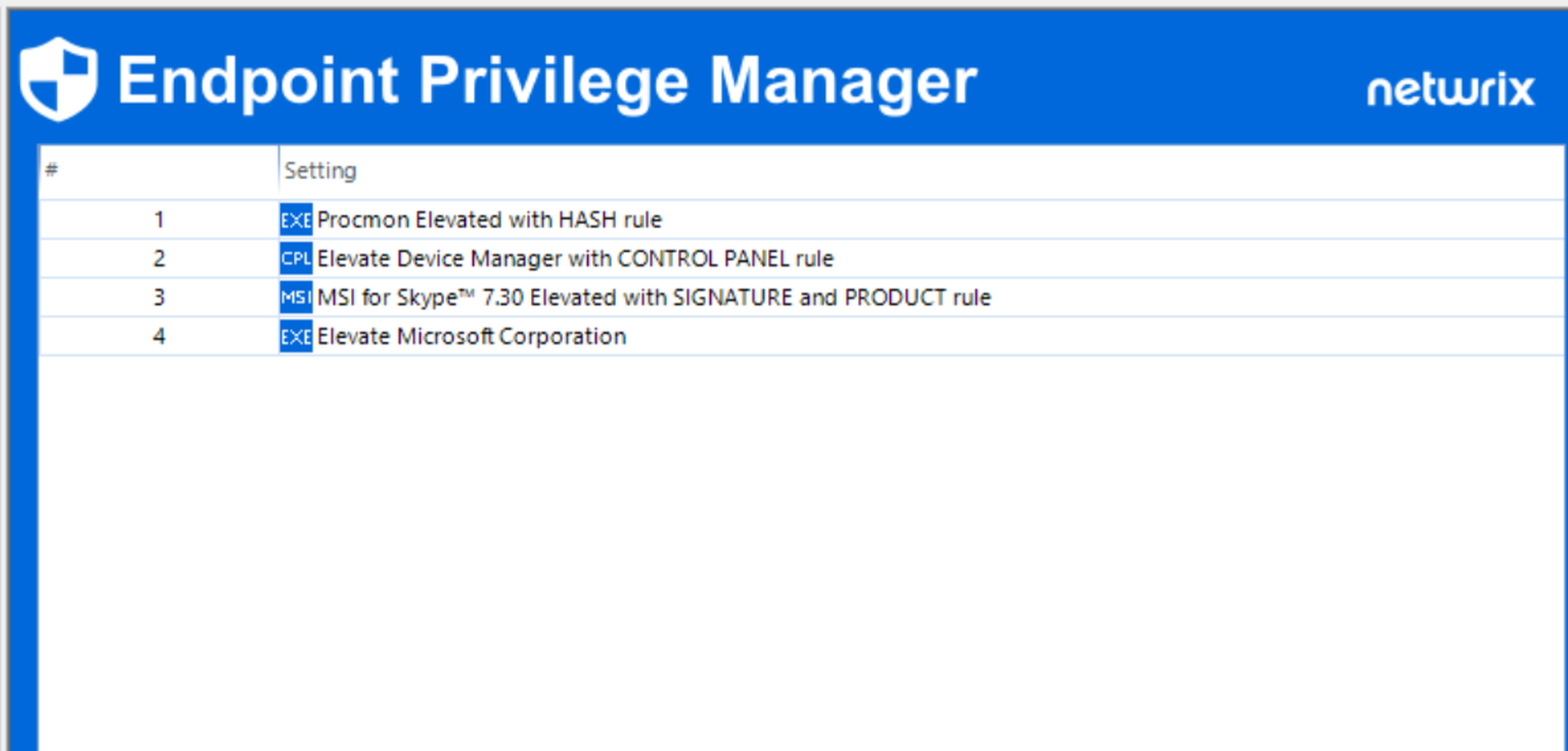
Are excessive user privileges putting your data at risk?
Local admin rights are still far too common, and they're still one of the top ways attackers gain a foothold. Whether users are installing unauthorized software, bypassing security policies, or clicking the wrong thing at the wrong time, unmanaged privilege creates avoidable risk.
Netwrix gives you a smarter way to lock down privilege, without locking out productivity.

Elevation without compromise
Allow users to install printers, run sanctioned installers, or change network settings — without ever becoming an admin.

SecureRun™
Block ransomware and unknownware automatically. Only trusted apps (based on file owner or policy) are allowed to run.

Granular privilege control
Create rules that elevate specific tasks, apps, file types, or commands — tailored to roles, departments, or scenarios.