Black Friday is that day of the year when consumerization is at its peak. Everybody is searching for bargains, many even take a day off and, in many US states, it has been declared a public holiday. That means something.
The shopping buzz has determined in the last few years an increase in cyber attacks due to poor data security knowledge, and more creative and sophisticated methods used by attackers.
With a high shopping fever syndrome, people will spend hours online on various e-commerce websites, to take full advantage of Black Friday and the weekend offers, but they will unwittingly put at risk their private data and their employer’s data security, because many people search for deals from the work computer, on the company network, or from home, where protection is weaker.
The number of phishing attacks, especially against payment systems and online stores will start to bloom with Black Friday and will continue to rise during the jolly shopping season of the winter holidays.
SimilarWeb’s UK Retailer Report revealed that in 2015, Black Friday visits for retail giants increased considerably – eBay had 3,858,000 visits from desktops and laptops, and 6,010,000 mobile visits; while Amazon reached the number of 6,100,000 of desktop visits and 10,618,000 of mobile visits. The mobile traffic share reached 63% for Amazon and 58% for eBay.
While e-commerce websites prepare their big sales and financial institutions expect an increased number of transactions, cybercriminals are preparing for their next victims.
So what are the main data security threats both individuals and businesses will deal with during Black Friday and Cyber Monday?
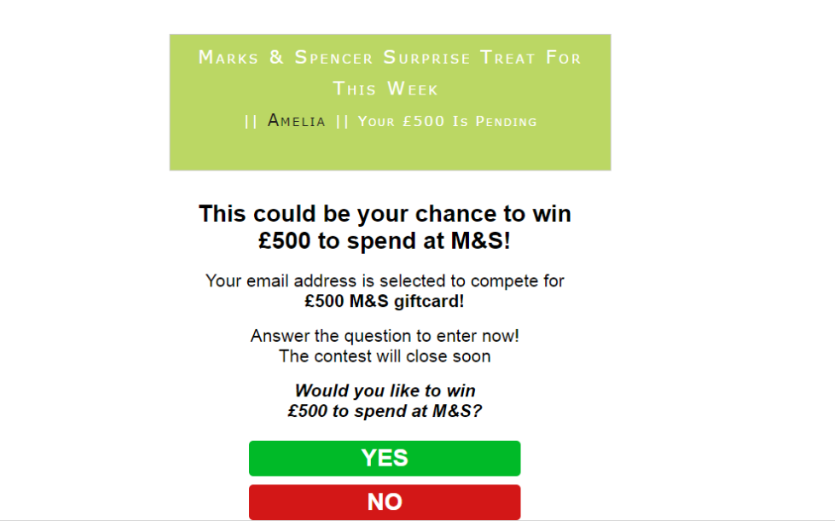
1. Fake payment pages or payment systems
Phishing pages of payment systems websites and banks can be easily created, perfectly imitating the original ones to steal payment data, like in the Visa and American Express’s case, which are most frequently duplicated. Consumers can be tricked to enter their credit card details on these fake pages and become cyber victims. To check if the page is legit or not, look closely at the URL. Fake pages have a different URL than the original ones or may slightly differ, ending with .net or .org. Do not enter your credit card information if you notice suspicious URLs to prevent your data from being stolen.
Another method to verify the authenticity of a website is to check if it uses Extended Validation SSL Certificate that displays a green address bar and the name of the certification issuer.
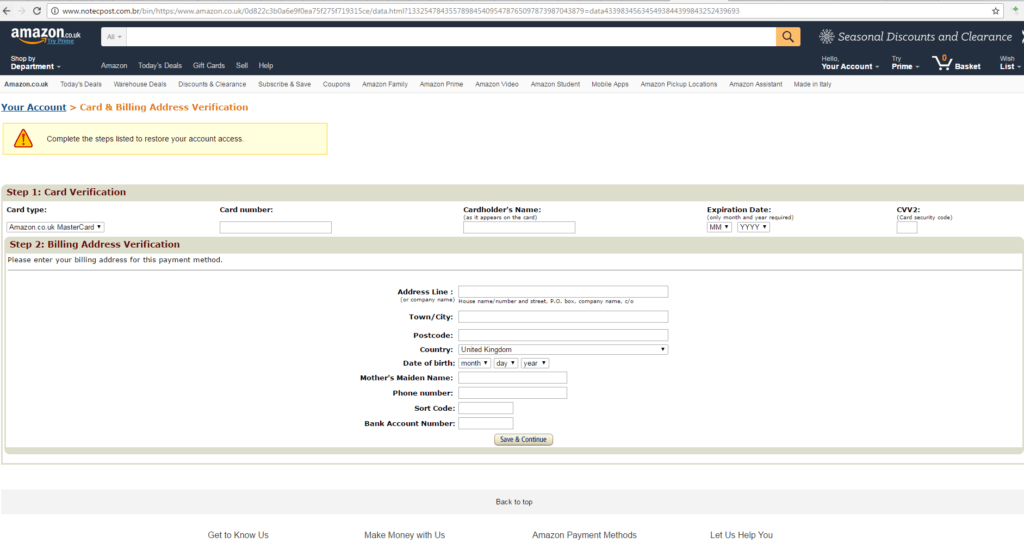
As can be seen in the screenshot above, the phishing copy of the Amazon shop quite precisely resembles the original website.
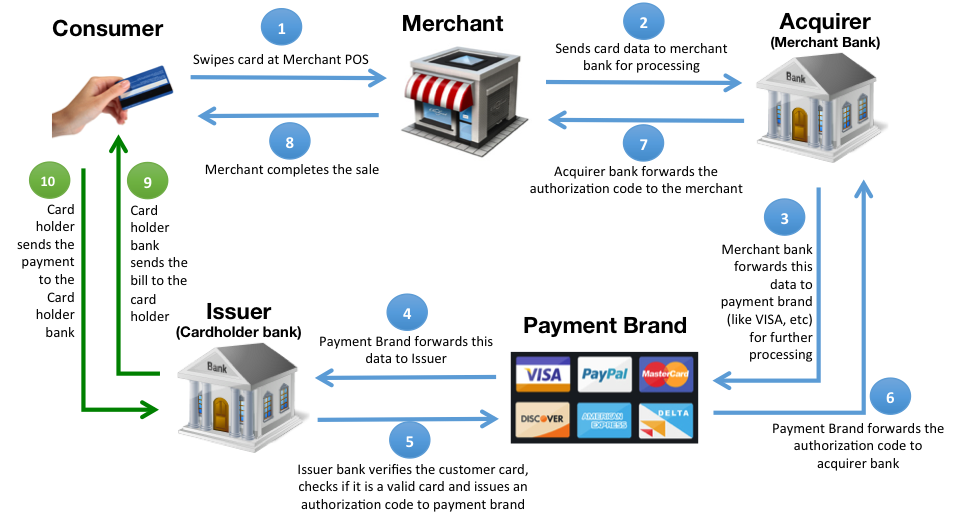
2. POS cyberthreats
POS terminals are highly vulnerable to attacks due to multiple inter-connected systems – servers, payment processors, websites, cash registers and others. POS devices should be protected from cyber threats with a strong specialized security solution, encryption should be put in place for all data moving back and forth. A recent example of a POS data breach is Oracle’s MICROS Point-Of-Sale.
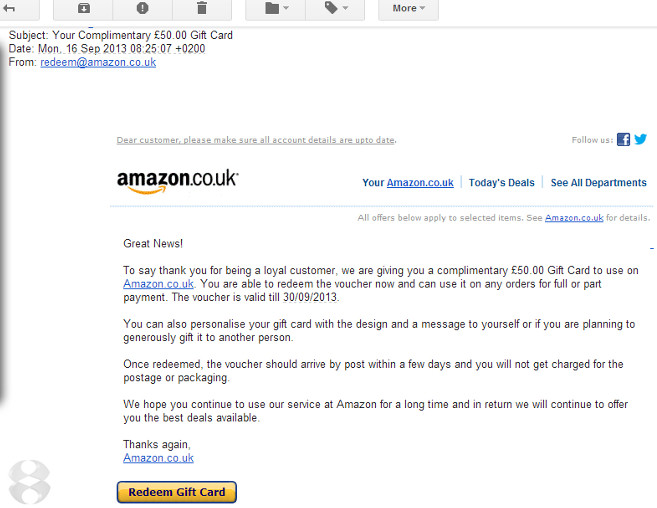
3. Phishing e-mails
Most of the data breaches result from an e-mail phishing attack. Employees can be tricked with these malicious e-mails, especially during the holidays, putting their identity and their financial assets at risk. The latest trends in phishing are the Amazon scam emails, which trick customers informing them there is a problem processing their order and it cannot be shipped, asking for their account details and accessing their financial information. Be extra careful when you open your emails. A good indicator, just like in the case of fake pages, is to look at the URL in the button, link that is included in the e-mail to notice if it’s the legit domain of the retailer.
4. Malicious links on social networks
Suspicious links containing malware can be sent by friends on social media networks like Facebook or Twitter and once clicked, they can infect your computer or mobile device or redirect you to a phishing page. Some accounts that send these links are not even real, in fact, they are computer bots. Keep an extra eye on what links you get.

5. Banner ads scams
Super deals that are advertised in banner ads can be fake. Criminals attack ad servers and redirect you to malicious sites, trying to steal your credentials. So think twice before clicking on the 1st ad with a surreal deal you see.
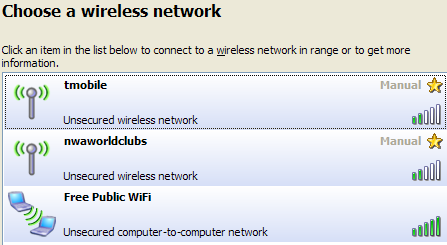
6. Unreliable Wi-Fi networks to make online payments
There are many free public Wi-Fi networks, but not all of them are secure. We advise you not to use them, especially when you want to make an online payment because man-in-the-middle attacks can easily capture traffic.
Regardless of the type of Wi-Fi you connect to, it’s important to be aware of a few Do’s and Don’ts when out and about on a Wi-Fi enabled device (Wi-Fi Network advice credits: reviversoft.com – How to Stay Safe on Public Wi-Fi Networks).
- DON’T automatically connect to anything that’s not your home Wi-Fi. You know how your device will auto-connect to anything that says AT&T? Not a good idea. Why? A rogue, invasive Wi-Fi signal can simply name itself after the most commonly used IDs, and devices will stupidly connect to them automatically, opening the device up to hacks.
- Anything that says “Free Public Wi-Fi” is likely a joke at best, and a phishing attempt at worst. Phishing means they are trying to hook you into making a mistake before taking control of your device or planting malware.
- DON’T connect to anything with this name.

Notice how Free Public Wi-Fi is peer-to-peer? A clear warning sign not to connect. - DO stick to secured Wi-Fi if possible, or unsecured Wi-Fi that requires a sign-in. Free Wi-Fi that has no sign-in policy is bad news.
- DON’T share files or folders across the public Wi-Fi network, such as in a Guest folder. You don’t want to give anyone else access to anything they’re not supposed to have. If you have File & Folder Sharing or Internet Sharing turned on, turn it off before you connect.
- TRY NOT TO visit any really sensitive websites while on public Wi-Fi, like bank accounts or shopping websites or even personal e-mail. That last one is difficult to avoid, so make sure you’re on the secure version of webmail (noted by the https: in the address and the little lock icon in the corner of your browser).
- DON’T leave your device unattended while in a public setting. Other than the possibility of theft, someone could look up personal info with just a few clicks while you’re away from the table.
- DON’T try to stream video, download gigabytes of data or do anything too Internet-hungry, as Public Wi-Fi generally doesn’t have bandwidth to spare. That means you don’t have the upload / download speed you’re used to at home. Airline Wi-Fi even specifically disallows video.
7. HTTP:// websites
If you intend to purchase something online, you should make sure you shop on sites that begin with HTTPS:// for secure communications, instead of HTTP://. Sensitive data like the credit card info you send to the retailer will be encrypted, decreasing the chances to be stolen.
8. Malicious files
Do not store, download or open suspicious files on your devices and computers and make sure your security solutions, like the antivirus, are in place and updated. Follow these rules for USB storage devices as well. They can bring malware on your computer, so do not connect thumb drives from unknown sources.
As a consumer, you can prevent disasters by paying attention to some small, but important details, like mentioned before, the URL of the website, the payment page, or the link in the phishing e-mail; you should also consider preparing a debit card that you can use only for shopping so, in the worst case scenario, you would lose just the amount of money you have at that point.
As a company, be prepared for employees to shop within the work schedules and from work computers or smartphones outside of the office as well. Update your security systems, make sure employees are aware of the risks, and encourage them to use VPNs. And…just in case business records are also on sale on the dark web for Black Friday, you might also consider implementing a Data Loss Prevention solution to prevent data leakages or thefts.
We wish you safe shopping and a Black Friday with no incidents!
Download our free ebook on
Data Loss Prevention Best Practices
Helping IT Managers, IT Administrators and data security staff understand the concept and purpose of DLP and how to easily implement it.