
In 2016 – the year of IoT innovations, wearable technology, and cloud computing – we have discovered some interesting facts. What is considered by many an “old-fashioned”, obsolete or close to extinction tool – the USB storage device–plays an interesting role in today’s work environment. Aside from the many customers that have implemented our USB device control solution to monitor and control how portable storage devices, like USB thumb drives, are being used, we also wanted to get a pulse from the 2016 Infosecurity visitors. Therefore, one of our main objectives as an exhibitor at this year’s event, on top of showcasing our DLP and MDM solutions, was to gather more information about visitors’ policies towards the use of USB devices. We conducted a research by surveying 180 respondents working in organizations from different verticals, most of them from the UK, but other regions as well, and with different roles. What we found out confirmed our perspective, but also surprised us at a certain level.
Key discoveries
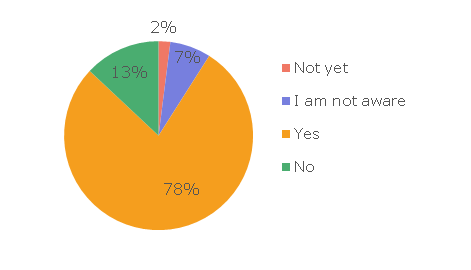
1. Most organizations have a data security policy in place
More specifically, 78 percent of the respondents answered yes, when asked if there is a data security policy in place in the company where they work. 13 percent said their company does not have one, 7 percent said that they were not aware, and 2 percent that they are planning to implement one. Of the 13 percent that had no security policy in place, most were small companies, with fewer than 50 endpoints in the network, and from these, startups with 3-5 computers mentioned they consider it unnecessary to implement a data security policy.
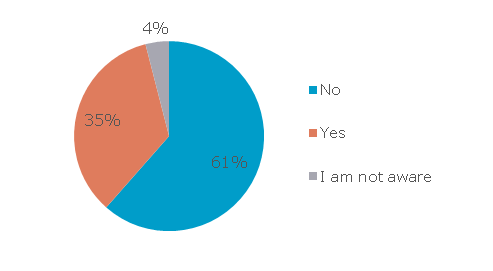
2. Encrypted or not, USB devices are allowed in company networks
74 percent of companies allow employees to use USB devices in their networks. From the total number of participants in the research, 35 percent force employees to use encrypted USB devices, while 61 percent do not enforce encryption. A further 4 percent of the respondents were not sure whether they should use encrypted USB devices or not. These stats show that USB devices are still very popular among employees and the fact that 61 percent of respondents admitted they are not forced by the IT department or organization policy to use encrypted devices makes them a big threat for companies’ confidential data.
3. 65 percent of the employees use USB sticks to transfer company files
74 percent are allowed to connect USB devices to their computers, 65 percent actually use them to transfer company files and USB thumb drives are constantly improved with bigger storage capacity and higher transfer speeds. Therefore, we can safely say they represent a vulnerability for data security and exposes organizations to potential data leakage and data loss.
4. Admitting to having lost a USB device with sensitive data is always difficult
Yet, 29 percent of the inquired visitors admitted and panic was the first feeling they had when they realized they had lost valuable personal or company data. 56 percent said they did not lose any USB device, 2 percent were not aware if they did or not and surprisingly, 13 percent mentioned they know at least one colleague or friend that lost a USB device. For an organization, all hell can break loose if just one stick with critical business data is misplaced or lost, so, while it is difficult to correct the nature of human beings to lose stuff, IT departments can resort to encryption to at least make sure no one will be able to access company’s vital data.
5. Conscience and companies’ policies align to tell people to alert the IT department if they lose a USB thumb drive with critical business data
When asked how they reacted when they realized they lost an unencrypted USB device with company data, 55 percent of the ones that admitted having lost a pen drive said they alerted the IT department (after the panic attack), 19 percent of them didn’t tell anyone, 18 percent didn’t know what to do and 8 percent called their lawyers. We’re wondering how many worldwide lost USB devices remain unreported and from the ones that are reported, what can the IT department do if those devices are not encrypted.
The 180 respondents are part of organizations from the following verticals: 19 percent finance , 15 percent government, 14 percent education, 13 percent IT / Telecom, 12 percent services / consultancy, 11 percent retail, 9 percent health care, 4 percent NGOs, and 3 percent recruitment. 90 percent of the companies where respondents work are based in the UK, 5 percent in France, 3 percent in Germany and 2 percent in Hungary.
Respondents’ roles in the organizations are the following: 48 percent IT Administrators, 15 percent Sales / Marketing, 13 percent security staff, 9 percent non-technical (other than sales/marketing), 7 percent top management, 4 percent software developers and 4 percent IT Managers.
Surprisingly enough, within the same period, we received information about how popular the USB blocks in the format of cover that is physically blocking inserting USB devices, are getting in some regions. If we are still facing threats from “old technology”, maybe we should approach it in a better way. The IoT era is here, so use technology to easily protect data. Device Control solutions have been enhanced in the last few years to fit multiple scenarios and infrastructures. For many businesses, it is not longer an option to completely block USB ports or other exit points. Rigid policies cause employees’ complaints about not being able to perform simple tasks. Before implementing a Device Control solution, make sure it provides granular and flexible policies, with the possibility of uniquely identifying portable storage devices, to create white lists, to establish rights per device, user, computer or groups and to monitor and block if necessary sensitive data being transferred to devices. Additionally, you should check if some type of encryption can be enforced, so data cannot be accessed if devices are lost or stolen. Besides controlling the use of portable storage devices, you should also focus on the content that is being transferred. For content-level control, Content-Aware Data Loss Prevention does the trick. It scans files being copied on removable devices and blocks the transfer in case sensitive content is detected.
What’s the policy in your company towards USB devices?
Download our free ebook on
Data Loss Prevention Best Practices
Helping IT Managers, IT Administrators and data security staff understand the concept and purpose of DLP and how to easily implement it.
















