Endpoint Protector Basic
Data Protection for Small Offices or Home Use. Endpoint Protector Basic is designed to protect your standalone computer from data theft. If you leave your Windows computer / Mac unlocked, someone else might access it and take away important data on their USB flash drives or other portable storage devices. With its ability to uniquely identify devices, you can be sure that you are in control and no third party can use your USB ports to copy data from your computer or to place potential malicious files on it.
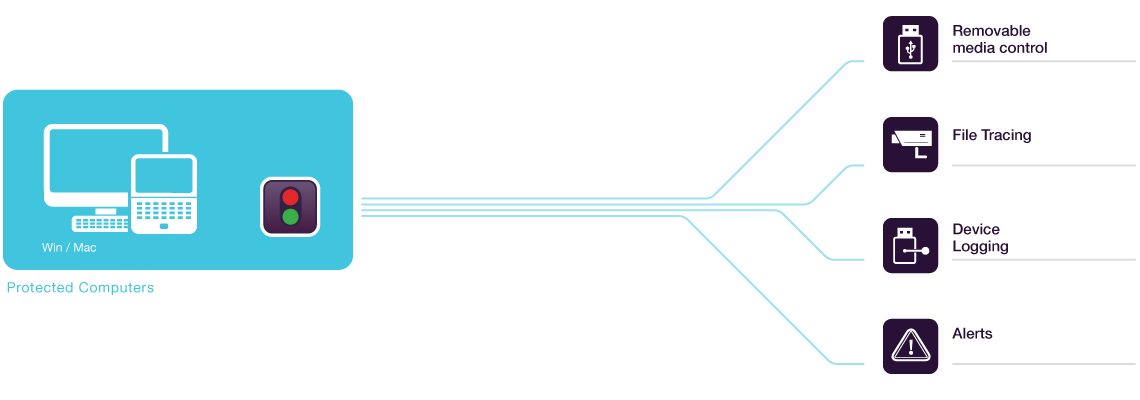
Device Control
With the administrative console, you will have a complete overview of all device activity, allowing for a close monitoring and control of USB flash drives and other portable storage devices.
File Tracing
The feature allows you to record what files are written or read from portable storage devices for later analysis.
Device Logging
All devices that are connected even if they are authorized or not are recorded in a log file for later reference.
Support for Windows and macOS
With Endpoint Protector Basic you can protect your computer whether it is a Mac or a Windows computer.
Endpoint Protector Basic Highlights
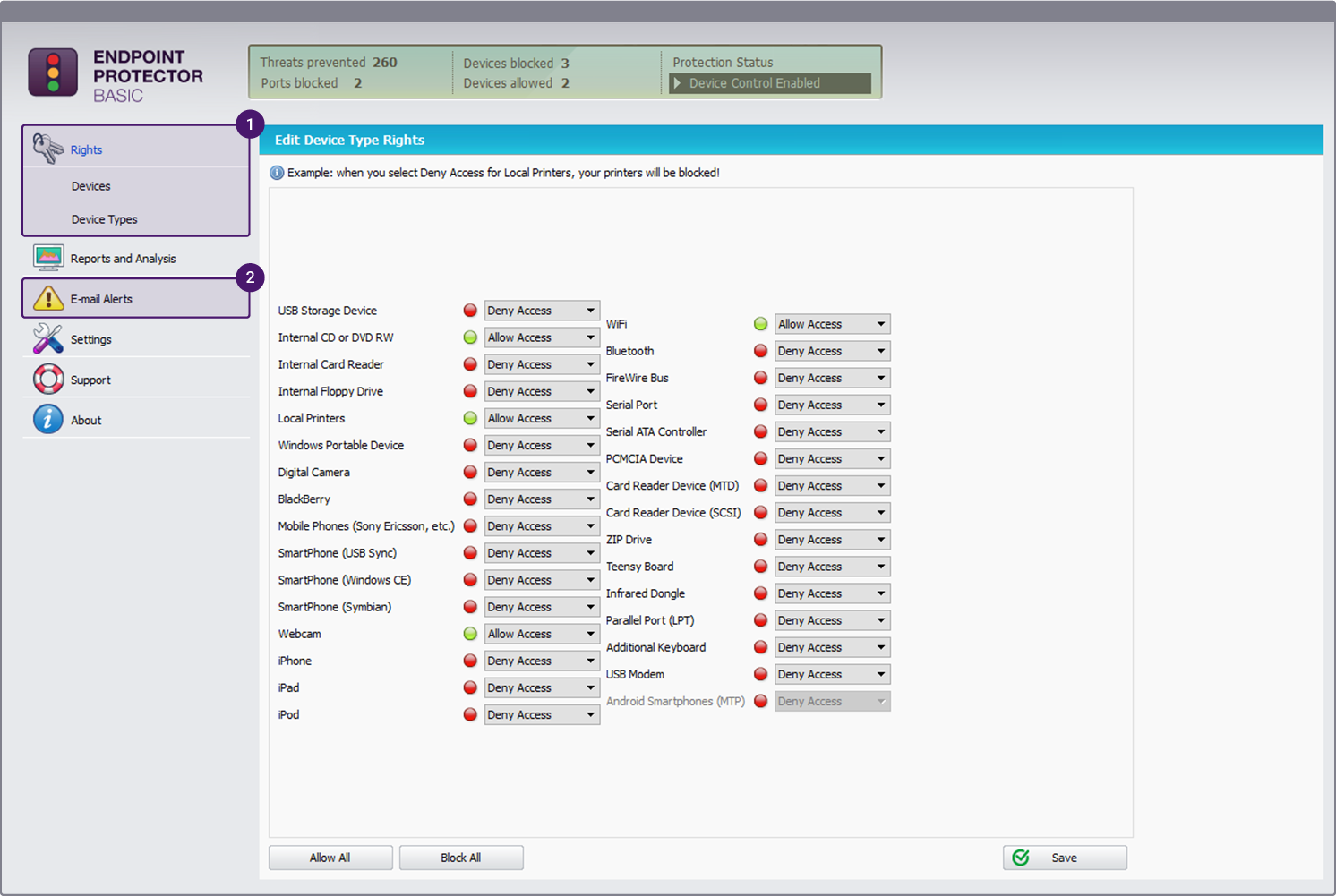
1
See a list of connected devices and approve, deny or assign Read-Only access for different device types and keep control of what devices are connected to your computer.
2
Set up e-mail alerts so you can receive notifications by e-mail if an unauthorized mass storage device was connected to your computer.
How Endpoint Protector Basic Works