Information
This only applies starting with 5.3.0.5 server version and 2.2.1.5 client version.
After the Endpoint Protector Client is installed and the desired Content Aware Policy is created, follow the next steps:
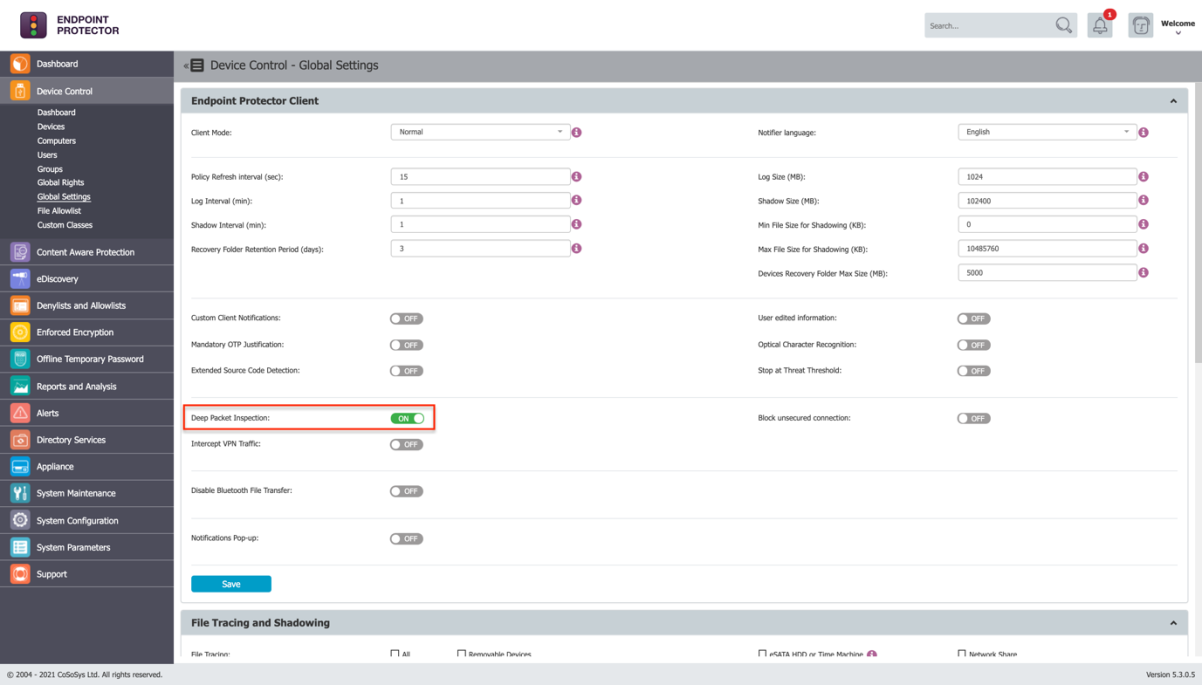
1. Reach Endpoint Protector Server and activate Deep Packet Inspection from the desired Device Control subsection: User/Computer/Group/Global Settings -> Manage Settings -> Endpoint Protector Client -> Deep Packet Inspection.
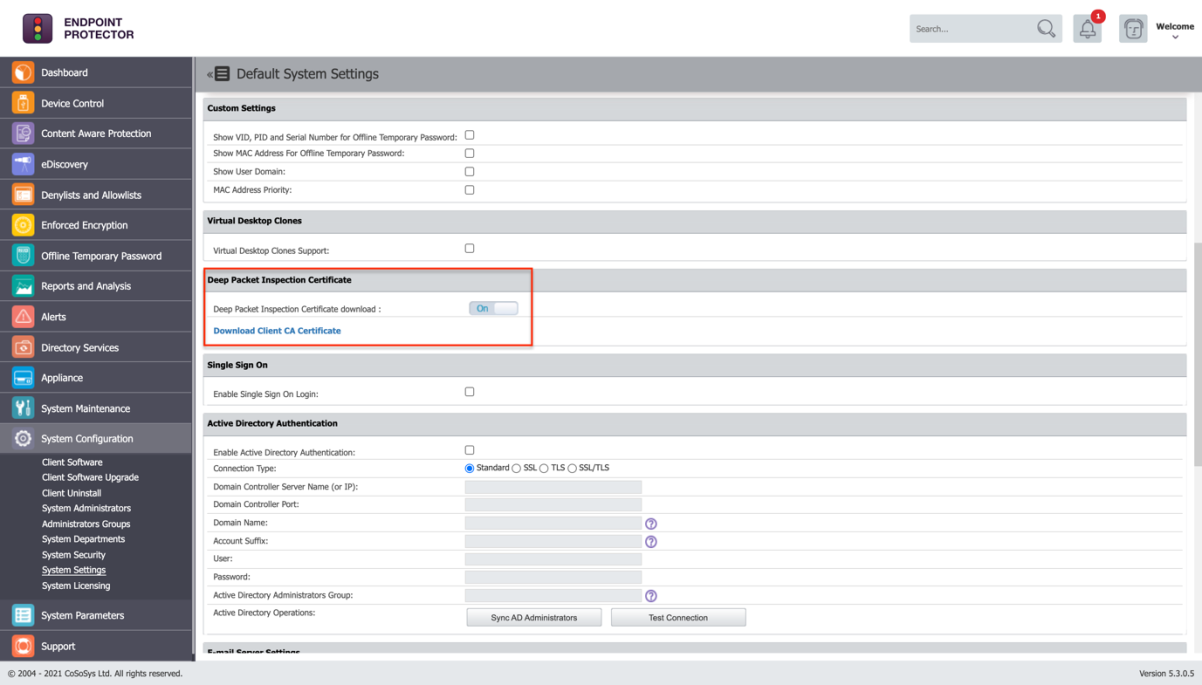
2. Go to System Configuration -> System Settings -> Deep Packet Inspection Certificate and download the CA Certificate.
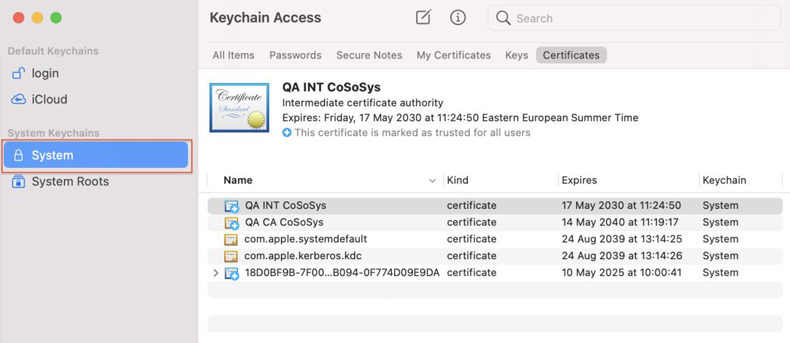
3. Open Keychain Access application from your macOS and make sure System is selected.
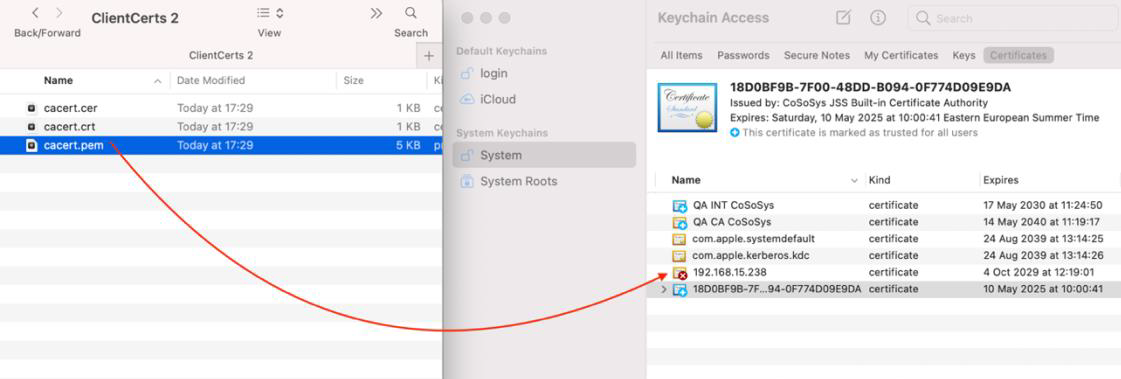
4. Decompress the downloaded ClientCerts file.
5. Select cacert.pem file and drag and drop it on Keychain Access - > System
6. The newly added certificate will have an ‘x’ on it. Double click on it and at Trust -> When using this certificate select ‘Always Trust’.
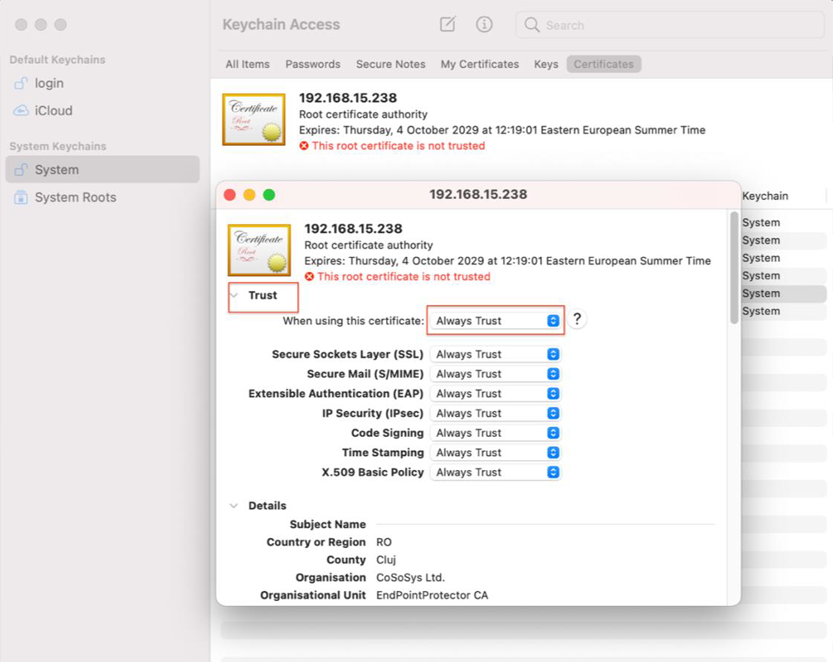
7. Save the changes.
8. Activate
Intercept VPN Traffic from the Endpoint Protector Interface.
9. Choose one option for
EPP behaviour when network extension is disabled.
Note
Temporary Disable Deep Packet Inspection: Deep Packet Inspection will be temporary disabled.
Block Internet Access: will cut the Internet connection until the end user will approve Endpoint Protector Proxy Configuration. The user will have the chance to allow it after a PC restart.
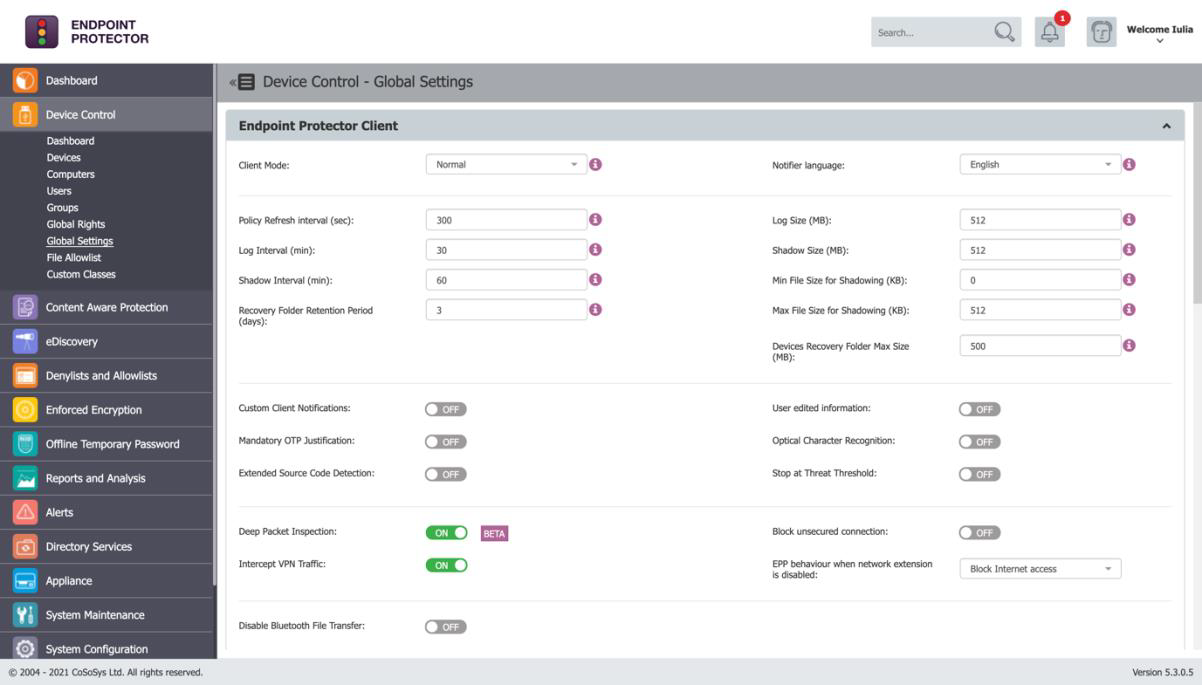
10. Save the changes.
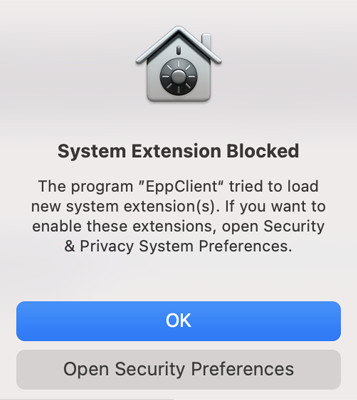
11. The following pop-up will be displayed informing the end user that a System Extension is blocked and needs to be allowed.
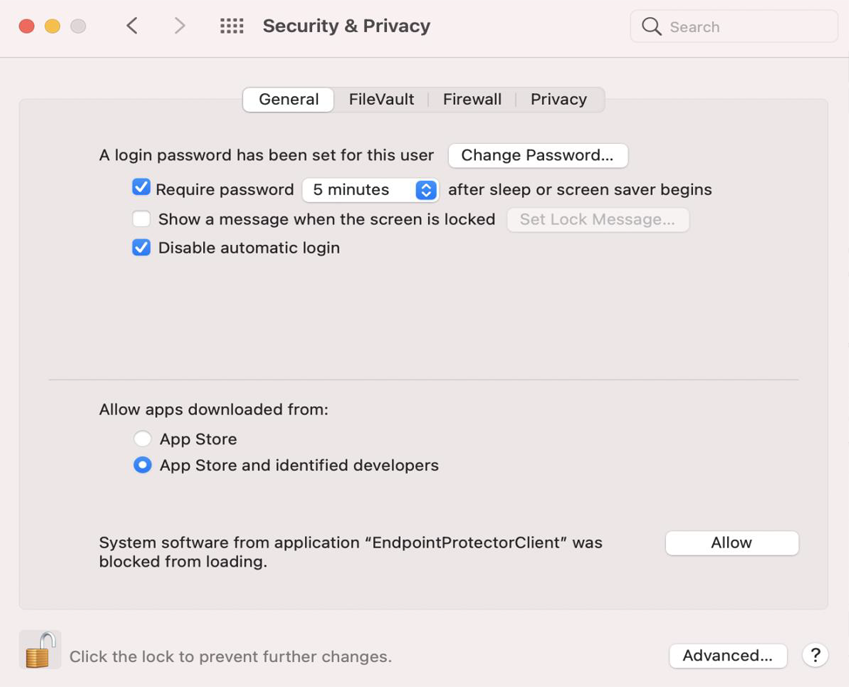
12. Go to System Preferences -> Security and Privacy -> General and allow the Endpoint Protector Client Extension.
13. The following screen is displayed and give Endpoint Protector Proxy Configuration Allow.
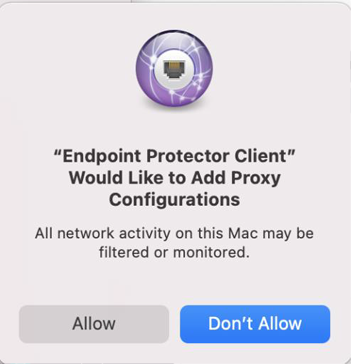
14. Intercept VPN Traffic is now successfully set.
15. It is recommended to disconnect and reconnect to the VPN after all these settings are taking effect in the Endpoint Protector Client.