Are Silent Configuration Changes Putting Your Data at Risk?
"Admin rights and malware aren’t the only risks—small, unauthorized changes to endpoint configurations can silently weaken security, violate compliance, or cause downtime.
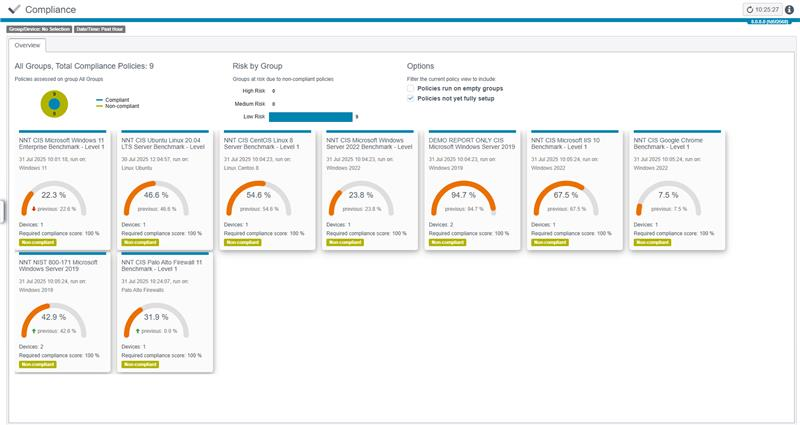
With Netwrix, you gain real-time visibility and control over endpoint configurations across your environment. Automatically detect drift, validate change intent, and restore secure baselines before issues spread."

Enforce known-good configurations
Use industry-aligned templates (CIS, DISA STIG, SCAP/OVAL) to define and deploy secure configurations for endpoints—faster than manual hardening.

Real-time drift detection
Get alerted to unauthorized or suspicious config changes as they happen—including GPO, registry, firewall rules, startup services, and more.

Eliminate change noise
Automatically suppress known, approved changes. Focus only on unexpected or risky activity—then respond with precision.