Compliance
Management & Auditing
With compliance regulations, there's always one more box to check. Let us handle the data security requirements.
- Effectively discover, monitor and control sensitive data
- We help with GDPR, HIPAA, PCI, CCPA, NIST and more
- #1 Cross-Platform coverage; including macOS, Windows, and Linux
Trusted by
Endpoint Protector Highlights
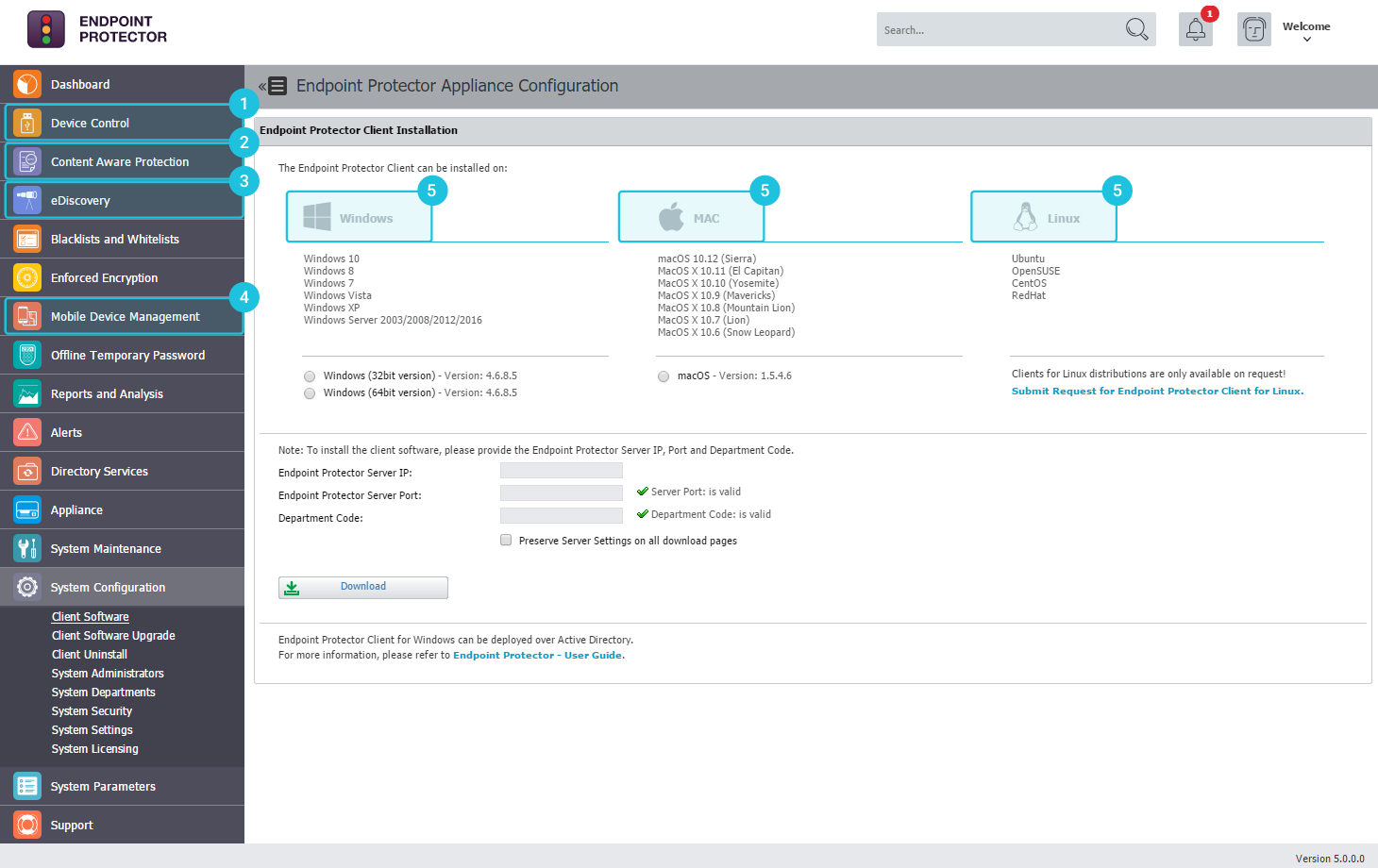
1
Seamless control of portable storage devices
Control and set rights for removable devices and ports in the Endpoint Management section and establish policies for users, computers and groups.
2
Monitor and block data transfers
Stop data leakage through the most common applications such as emails, browsers, and other online applications through the Content Aware Protection tab.
3
Cross-platform eDiscovery
Create policies to inspect data residing on protected Windows, macOS and Linux computers. Discover sensitive data at rest and encrypt or delete it.
4
Extend data security to mobile devices
Within the same management console, set up security policies for corporate or employee-owned mobile devices.
5
Protection for Windows, macOS, and Linux
Endpoint Protector takes cross-platform DLP to the next level. Protect data against loss and theft on all company's endpoints.
Josh McCown, IT Director, Spectrum of Hope