Is your company's
sensitive data at risk?
Don't wait to find out. Secure your data with Endpoint Protector Data Loss Prevention (DLP) Software.
- Industry-leading DLP for personal information and intellectual property.
- Deploy remotely to ensure security and compliance for employees working from home.
- Recognized as a premier solution in Gartner's latest Enterprise DLP Magic Quadrant
Trusted by
Discover, Monitor, and Protect Your Sensitive Data
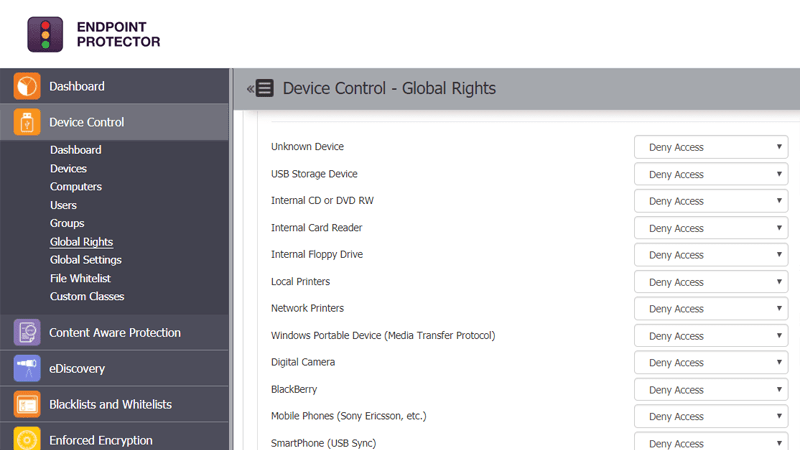
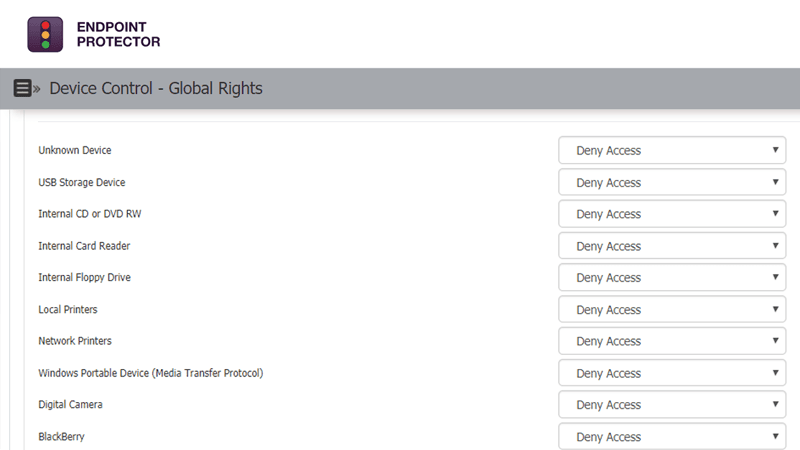
Device Control
USB & Peripheral port control
Define granular access rights for removable devices and peripheral ports and establish policies for users, computers and groups, maintaining productivity while enforcing device security.
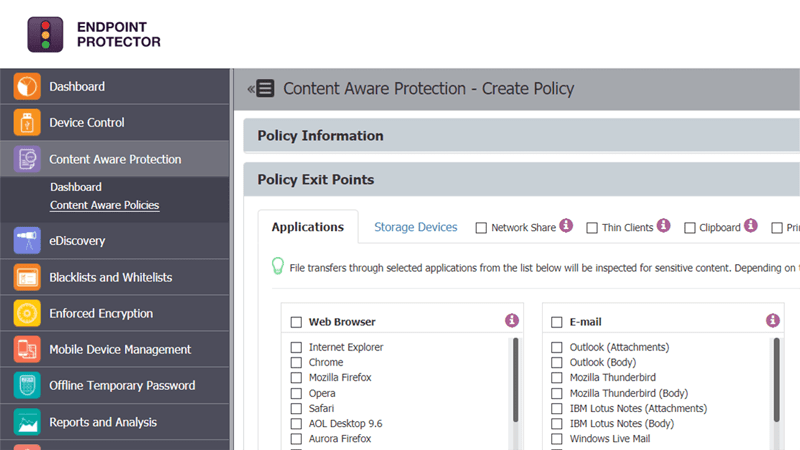
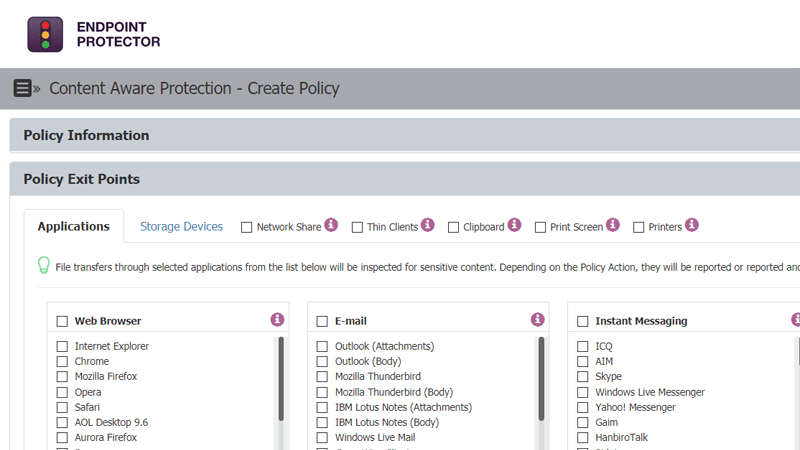
Content-Aware Protection
Scanning data in motion
Prevent data leakage through all possible exit points, from clipboard, screen captures, USB devices, to applications including Microsoft Outlook, Skype or Dropbox.
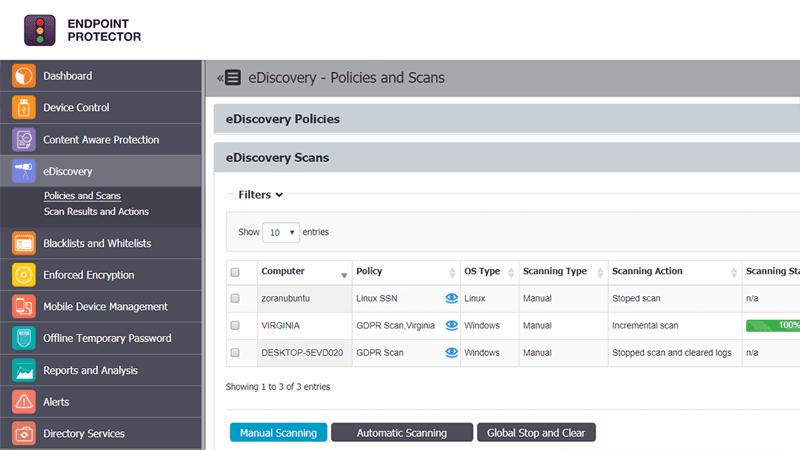
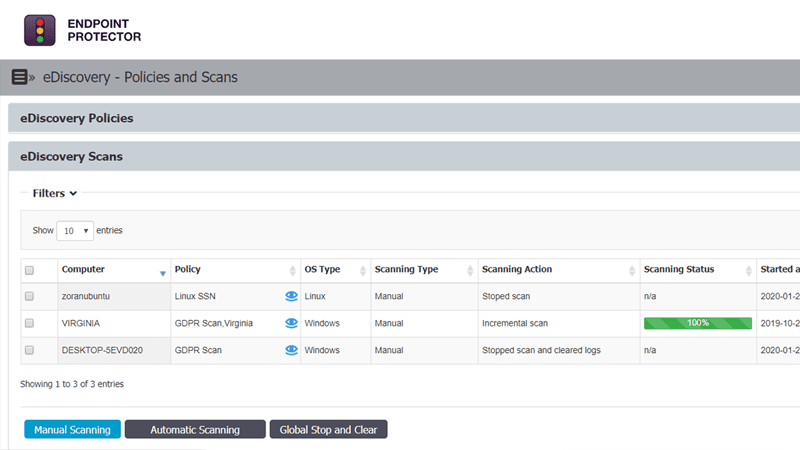
eDiscovery
Scanning data at rest
Prevent data breaches by scanning and identifying sensitive data at the endpoint level on Windows, macOS, and Linux computers. Ensure compliance with regulations like HIPAA, PCI DSS and others.
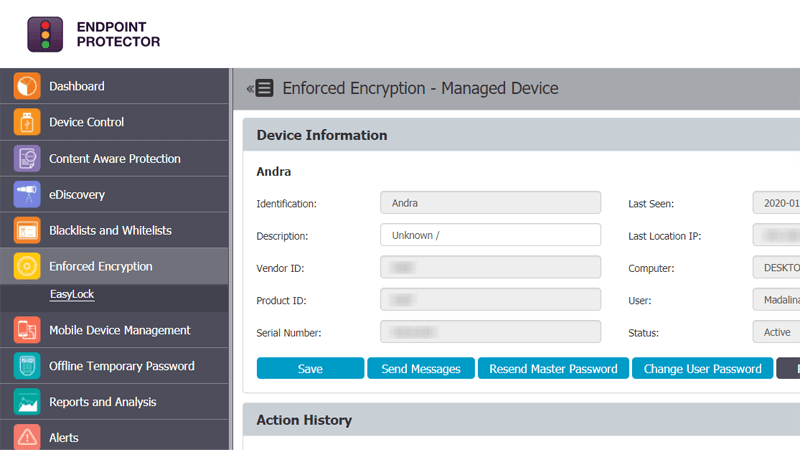
Enforced Encryption
Automatic USB encryption
Encrypt, manage and secure USB storage devices by safeguarding data in transit. Password-based, easy to use and very efficient.