Multi-OS DLP: Redefined Control and Compliance
Protect critical data and IP where it's most vulnerable – directly at your endpoints
- Granular control and policy customization
- Multi-OS compatibility
- Stay ahead of regulatory demands with ease
Award-winning enterprise DLP, recognized as a premier solution in Gartner's Enterprise DLP Magic Quadrant
See all awards & certifications



"Excellent support and product. Would recommend to colleagues who require a strong DLP solution."
G2 Reviews - 2025
Nicholas K.
IT Security and Network Specialist
Enterprise (>1000 employees)
"Great tool for enterprises"
G2 Reviews - 2025
Verified Endpoint Protector user
Information Technology and Services
Enterprise (>1000 employees)
"Endpoint Protector fills a gap for most companies."
G2 Reviews - 2025
Verified Endpoint Protector user
Defense & Aerospace
Mid-Market (51-1000 employees)
"Works perfectly for our organization"
G2 Reviews - 2025
Verified Endpoint Protector user
IT Services
Enterprise (>1000 employees)
Trusted by
Advanced DLP for the evolving enterprise landscape

Granular Control and Policy Customization
Endpoint Protector offers highly detailed device control that lets you restrict non-compliant devices while ensuring business continuity. You can create policies based on a variety of parameters, including device type, brand, and serial number, giving you unparalleled control and flexibility.

Proactive Compliance Management
Stay ahead of regulatory demands. Ensure compliance with regulatory frameworks including PCI DSS, HIPAA, NIST, ISO 9001, and GDPR.

True multi-OS solution
Enable seamless management of all endpoints, regardless if they run a Windows, macOS or Linux-based operating system. This wide platform compatibility ensures that businesses with diverse IT infrastructures can benefit from the same level of device control and security.
Comprehensive control and security for sensitive data
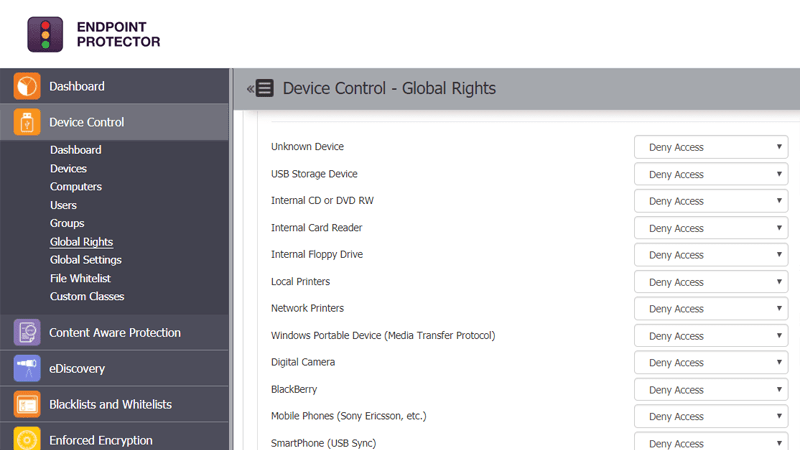
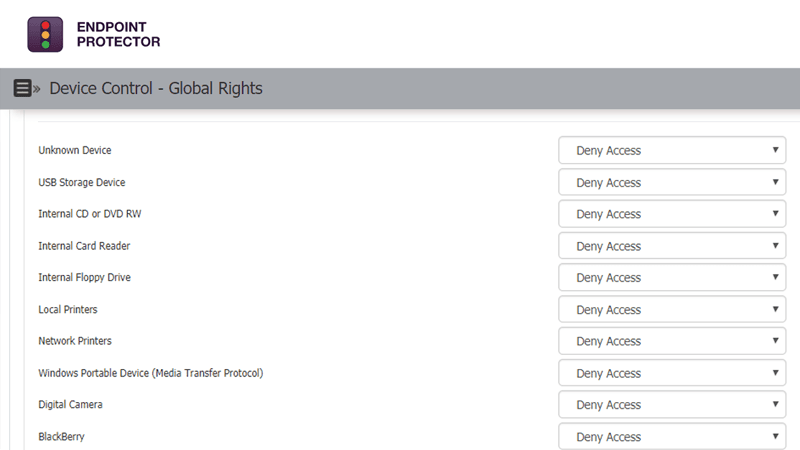
Device Control
USB & Peripheral port control
Define granular access rights for removable devices and peripheral ports and establish policies for users, computers and groups, maintaining productivity while enforcing device security.
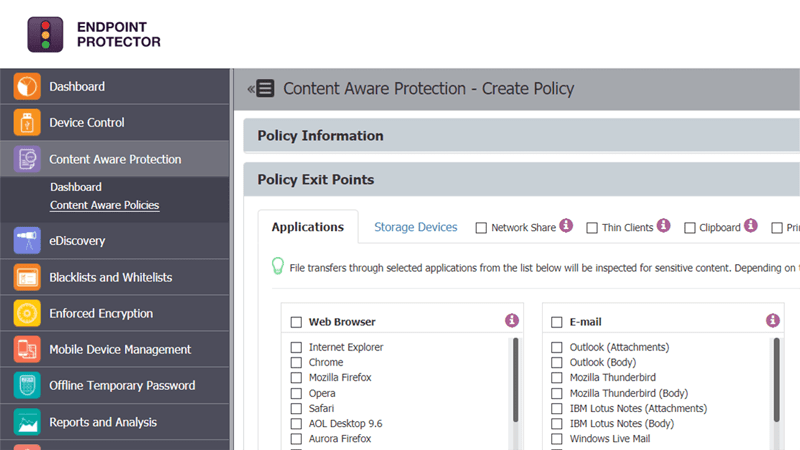
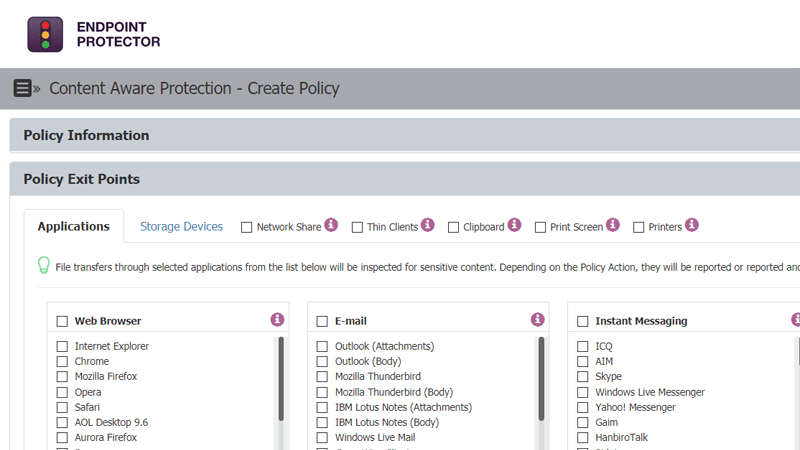
Content-Aware Protection
Scanning data in motion
Prevent data leakage through all possible exit points, from clipboard, screen captures, USB devices, to applications including Microsoft Outlook, Skype or Dropbox.
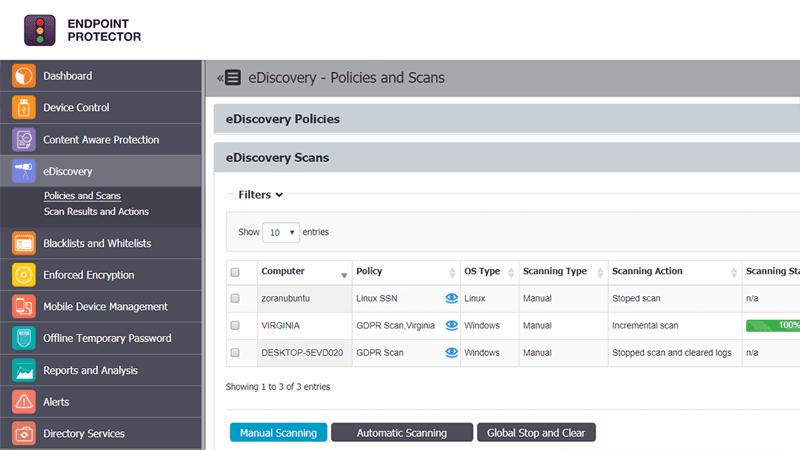
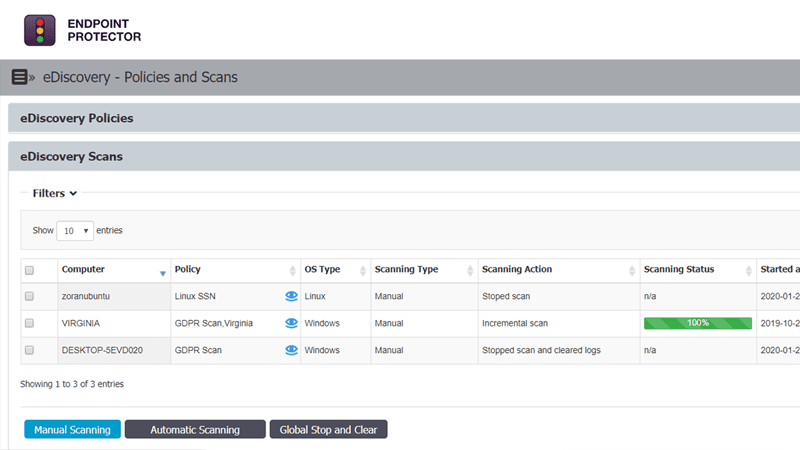
eDiscovery
Scanning data at rest
Prevent data breaches by scanning and identifying sensitive data at the endpoint level on Windows, macOS, and Linux computers. Ensure compliance with regulations like HIPAA, PCI DSS and others.
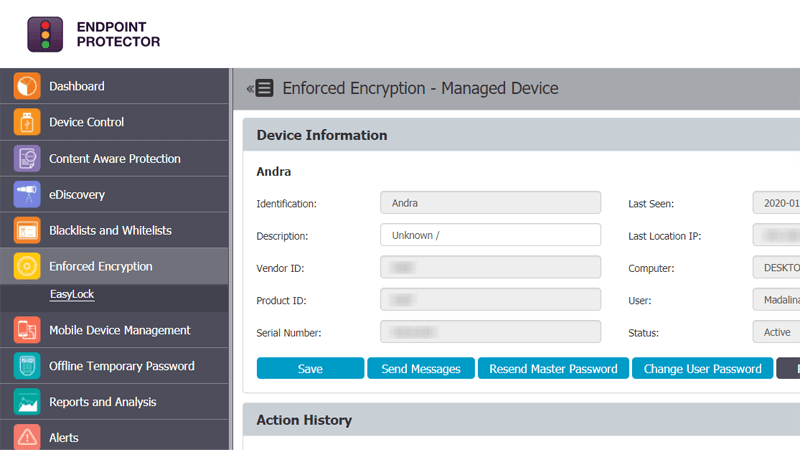
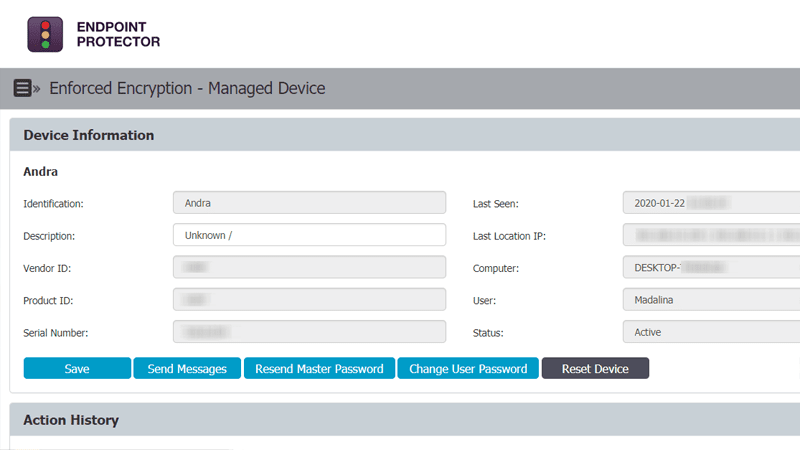
Enforced Encryption
Automatic USB encryption
Encrypt, manage and secure USB storage devices by safeguarding data in transit. Password-based, easy to use and very efficient.
Case study
SAMSUNG R&D Institute
The Challenge
Samsung’s R&D Institute needed a DLP solution that could help to manage insider threats and monitor employee activity related to data transfers.
The Solution
Samsung’s R&D Institute chose Endpoint Protector by CoSoSys because of its multi-OS capabilities. Besides Windows, Endpoint Protector efficiently safeguards sensitive data on macOS and Linux-based operating systems. What’s more, Endpoint Protector is the only enterprise DLP to offer same-day support for the latest macOS releases, closing any gaps in protection when new OS updates are made.
The team uses Endpoint Protector to control peripheral devices connected to employee machines (USB drives, smartphones, and more), and scans and protects data in motion with content inspection and contextual scanning. This prevents data leakage and data loss through various exit points, including web browsers, email clients, and applications such as Microsoft Outlook, Skype, or Dropbox.
Why Endpoint Protector?
- Cross-platform protection for Windows, macOS, and Linux computers
- Zero-day support for macOS and Windows
- User-friendly interface
- Granular control over PC peripherals and data transfers
“We have a good experience working with Cososys as a company. We’ve always received prompt support from the team.”
Info Security and IT
Intra development and Management