Is your sensitive data at risk due to a lack of device management?
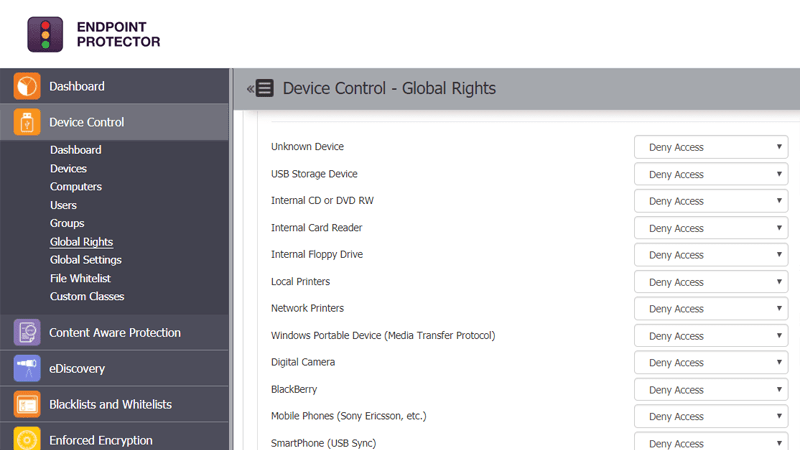
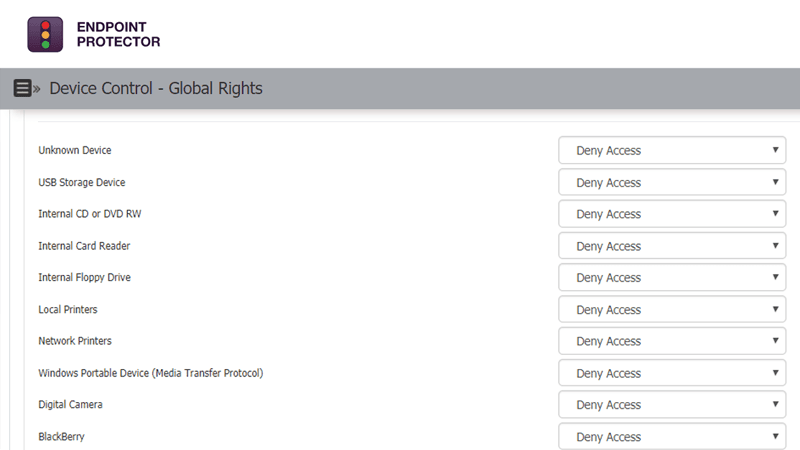
External devices such as flash drives, Bluetooth, and other portable USB devices, although harmless at a first glance, are one of the top causes for security incidents that can cause major damages to any business. Damages range from confidential data being stolen to huge fines due to violations of compliance rules and regulations. End users must be aware of the risks, and for businesses, to have measures in place to prevent data breaches and leakage from external devices.

Cross-platform, lightweight agent
Remotely monitor USBs and peripheral ports across different operating systems from a simple web-based interface with no performance impact on the protected computers. Set device control policies with ease for Windows, macOS, and Linux, and enable USB Device Control functionality to have precise and granular control over USB devices and other portable devices on each operating system.

Remote and temporary access
Grant USB access remotely, even when computers are offline, while having a complete list of log reports once back on the network.

Precise and granular control
Depending on departments’ requirements, specify which devices can or cannot be used, create device whitelists and blacklists, and define policies per user, computer, or group for uninterrupted workflow throughout the company.